User-attributed SAP writeback with OAuth 2.0
This page contains instructions for setting up the OAuth 2.0 server in SAP and setting up the OAuth 2.0 client in Foundry.
Setting up the OAuth 2.0 server in SAP
Prerequisites
- SP21 or above of the Palantir Foundry Connector 2.0 for SAP Applications ("Connector")
- The Foundry technical user in SAP should be a
SYSTEMuser /PALANTIR/OAUTH_CLIENTshould be assigned to the Foundry technical user and any end users wishing to write back to SAP from Foundry/PALANTIR/CONTENT_FUNCTION_ALLshould be assigned to end user- All services under the
/sap/public/bcnode to be activated (for OAuth 2.0 configuration)/sap/bc/sec/oauth2*/default_host/sap/bc/webdynpro/sap/oauth2_authority
- SAP Gateway is active
- SAP NetWeaver 7.4 SP09 or above (support for OAuth 2.0 and OData)
Reference
- Note 1688545 - OAuth 2.0 Server in AS ABAP troubleshooting ↗ (SAP login required)
- Help: OAuth 2.0 Server for AS ABAP ↗
OAuth 2.0 configuration
- Run the
SOAUTH2transaction. - Select Create....
- Enter the username of the Foundry technical user as the OAuth 2.0 Client ID.
- Select Next >.
- Enter the username of the Foundry technical user as the User ID.
- Ensure Client User ID and Password and SSL Client Certificate are both checked.
- Select Next >.
- Set the Redirect URI as
https://<FOUNDRY_DOMAIN>/workspace/oauth2-clients/callback. - Select Next >.
- Add a Scope Assignment with an OAuth 2.0 Scope ID of
/PALANTIR/SRV_0001and a description such asPalantir Foundry writeback using SAP functions. - Select Next > and then Finish.
OData configuration
- In the Maintain service page within SAP, follow the hierarchy of services to find opu > odata > palantir.
- Right-click on palantir and select Activate Service.
- Select Yes when prompted.
- On the Create/Change a Service tab, select GUI Configuration under Interactive Options.
- Add parameter with name
~CHECK_CSRF_TOKENand value0(zero). - Disable CSRF_TOKEN validation as outlined here: https://help.sap.com/doc/saphelp\_hba/1.0/de-DE/e6/cae27d5e8d4996add4067280c8714e/content.htm
- Run the
/IWFND/MAINT_SERVICEtransaction. - Select Add System Alias under System Aliases.
- Add a system alias with the following values:
- Service Doc. Identifier:
/PALANTIR/SRV_0001 - User Role: blank
- Host Name: blank
- SAP System Alias:
LOCAL - Metadata Default: unchecked
- Default System: checked
- Tech. Svc. Name:
/PALANTIR/SRV - Ext. Service Name:
ODATA_SRV - Version:
1 - User Name: blank
- Service Doc. Identifier:
Setting up the OAuth 2.0 client in Foundry
This follows the general approach outlined in Configure outbound applications but has been tailored specifically to SAP systems.
Source connection setup
Ensure that the SAP source URL is using HTTPS, or webhooks will fail when using an OAuth flow.
- Create a new REST API source.
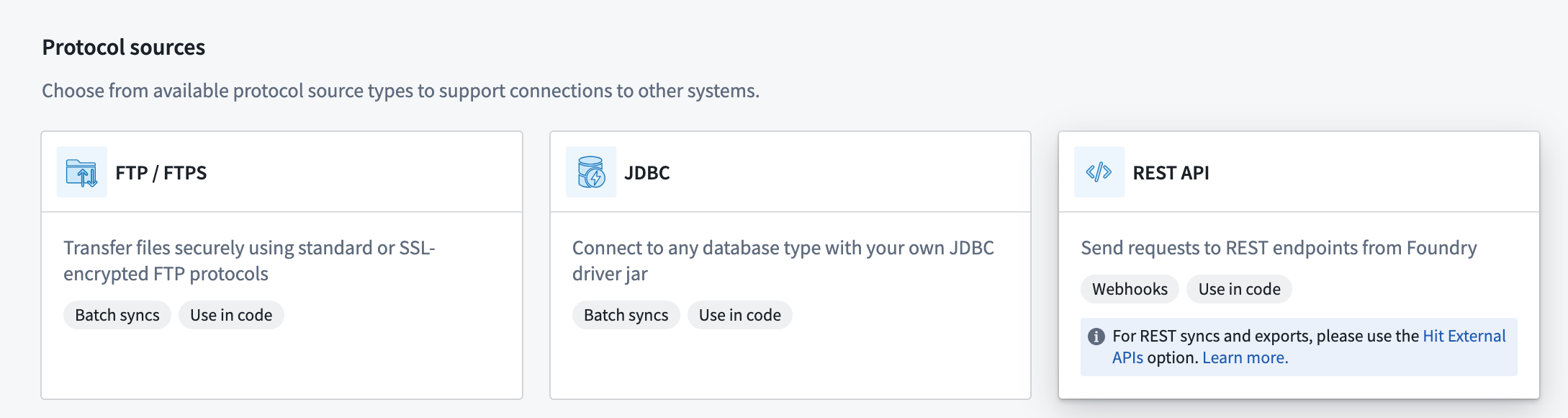
- Configure the source with the base domain URL and port used for the SAP source.
- Select Basic authentication and add the username and password used to connect to SAP.
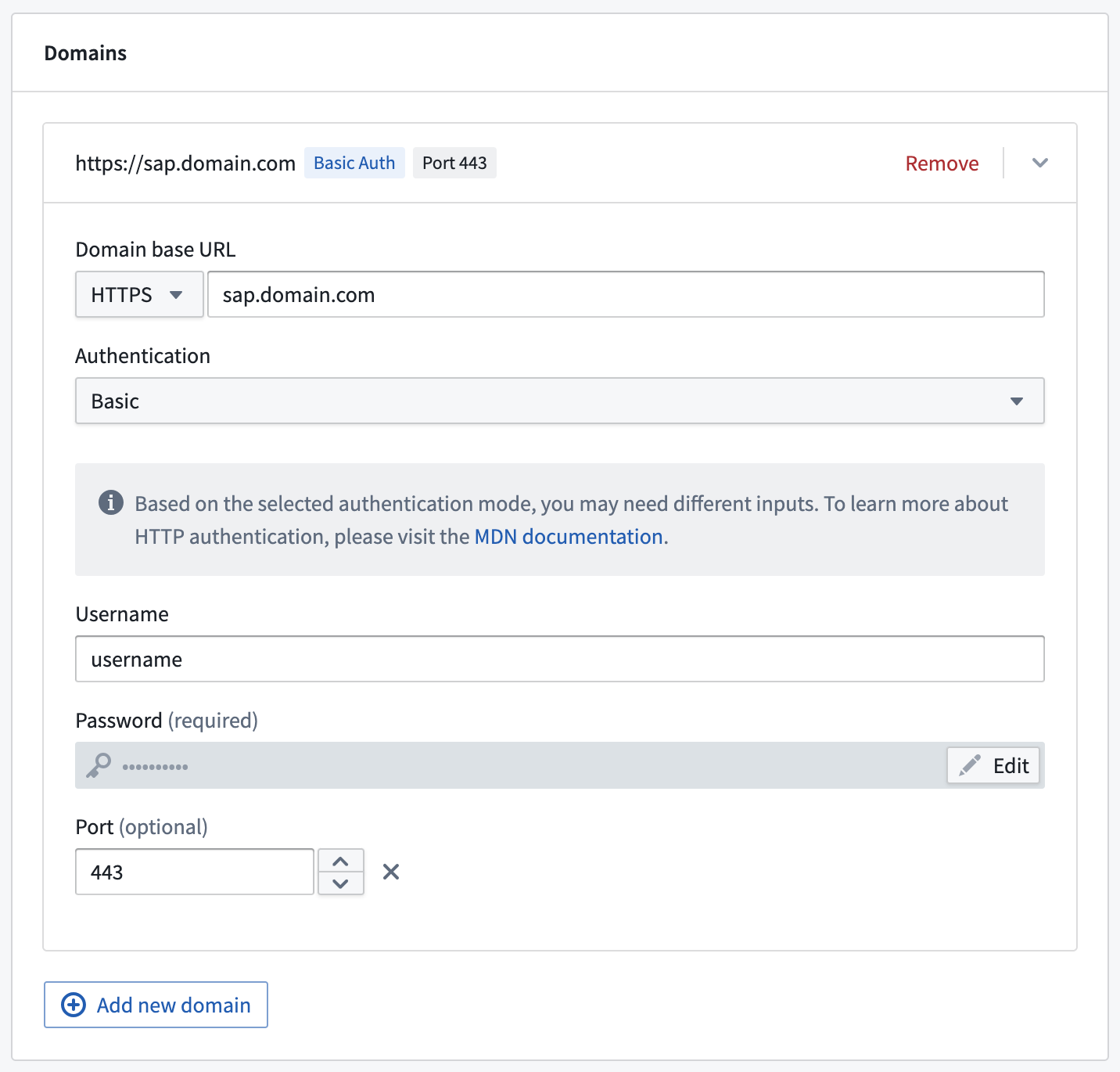
- Save the source.
OAuth 2.0 authorization flow webhook setup
-
On the overview page of the new REST API source, select Create webhook.
-
Give the webhook a name (such as “SAP OAuth2 authorization code flow webhook”).
-
Advance to the Request configuration step.
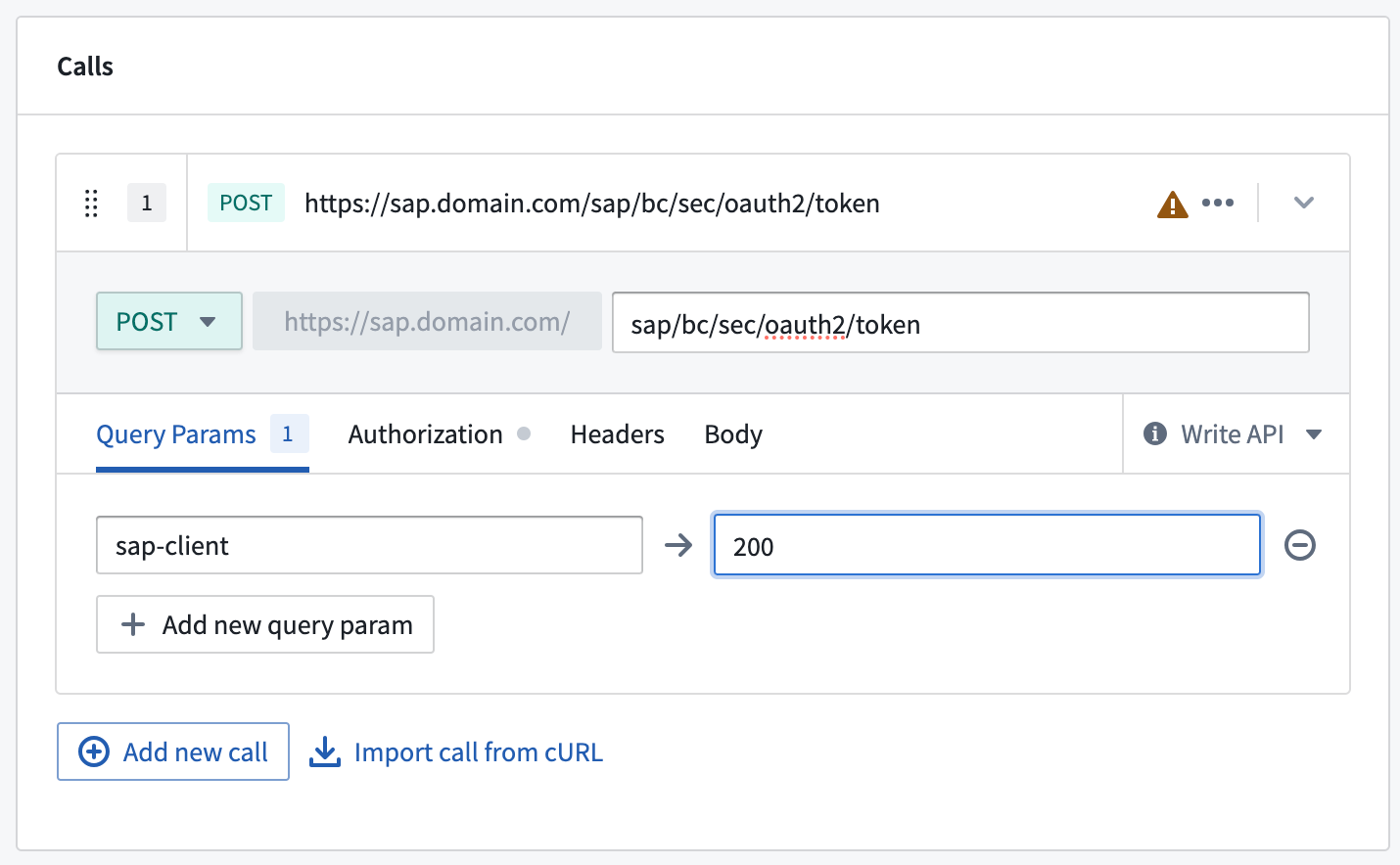
-
Under Calls, select POST as the request type and enter
sap/bc/sec/oauth2/tokenas the path. -
Under Query Params,
sap-clientmight have to be set if the client used is not the default client.
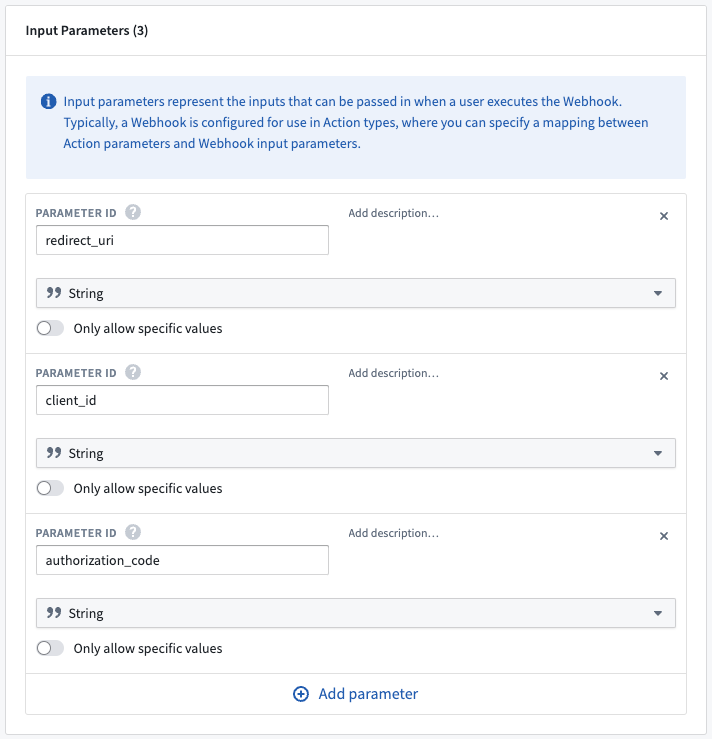
- Scroll down to Input Parameters and add the following three parameters (all string type):
redirect_uriclient_idauthorization_code
- Scroll back up to Calls and select the Body tab.
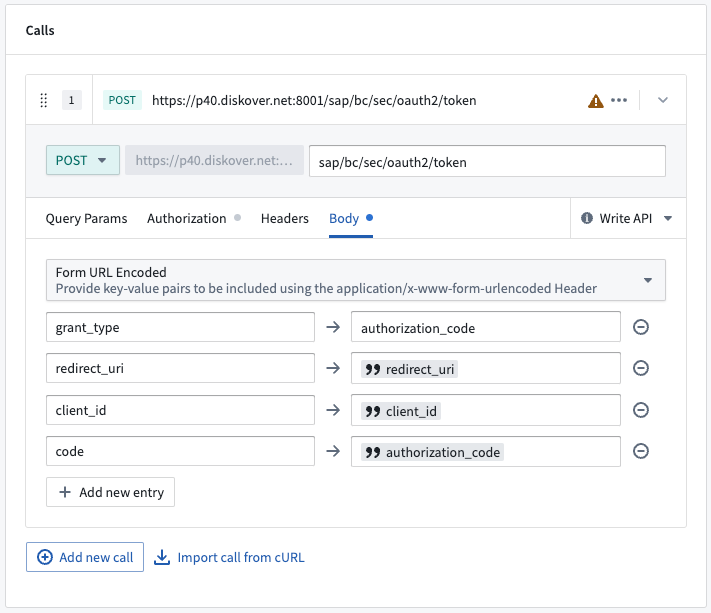
- Choose Form URL Encoded and add the following four entries:
grant_type→authorization_coderedirect_uri→ Mapped to theredirect_uriinput parameter (see below for how to do this)client_id→ Mapped to theclient_idinput parametercode→ Mapped to theauthorization_codeinput parameter
- To map an input parameter, type @ into the field and then select Input Parameter. Find the relevant parameter, select it and then select Add beneath.
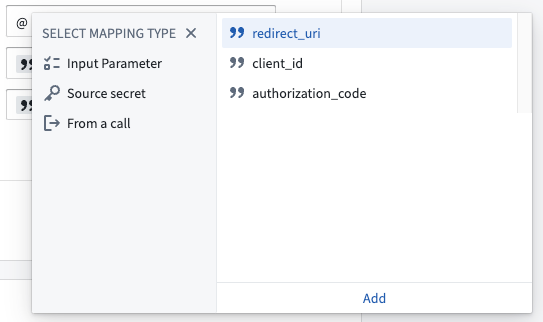
- The finished Body configuration should look like this:
- Advance to the Responses step.
- Create the following five Output Parameters. All should be of type string and should be extracted by key from the response.
access_tokentoken_typeexpires_inrefresh_tokenscope
This is an example for creating access_token. All output parameters should follow this pattern.
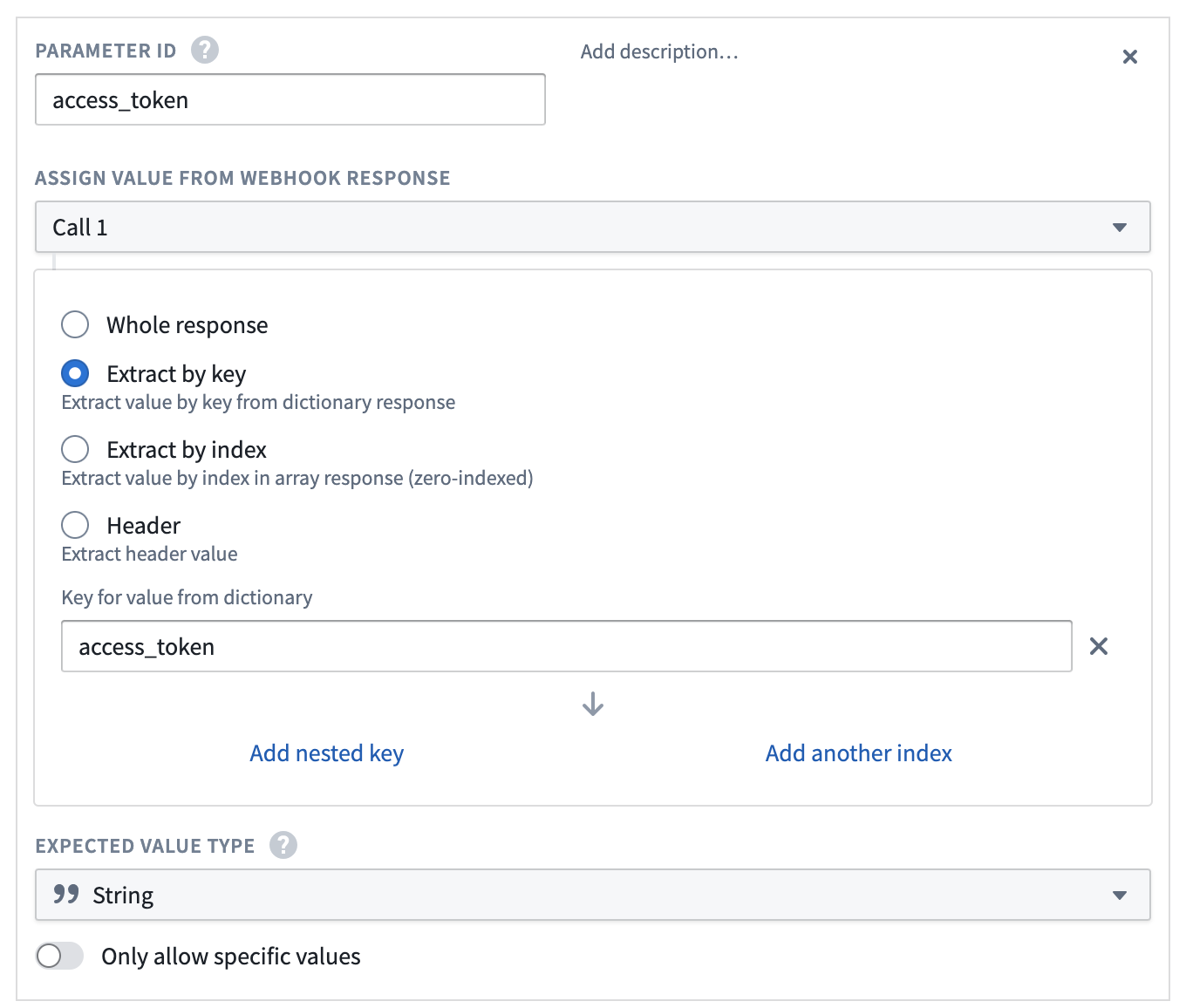
- Save the webhook by selecting Create webhook and continue.
OAuth 2.0 refresh flow webhook setup
- Create a new webhook from the REST API source.
- Give the webhook a distinct name (such as “SAP OAuth2 refresh flow webhook”).
- The request method should again be set to POST and the same path (
sap/bc/sec/oauth2/token) should be used. - As with the previous webhook, set
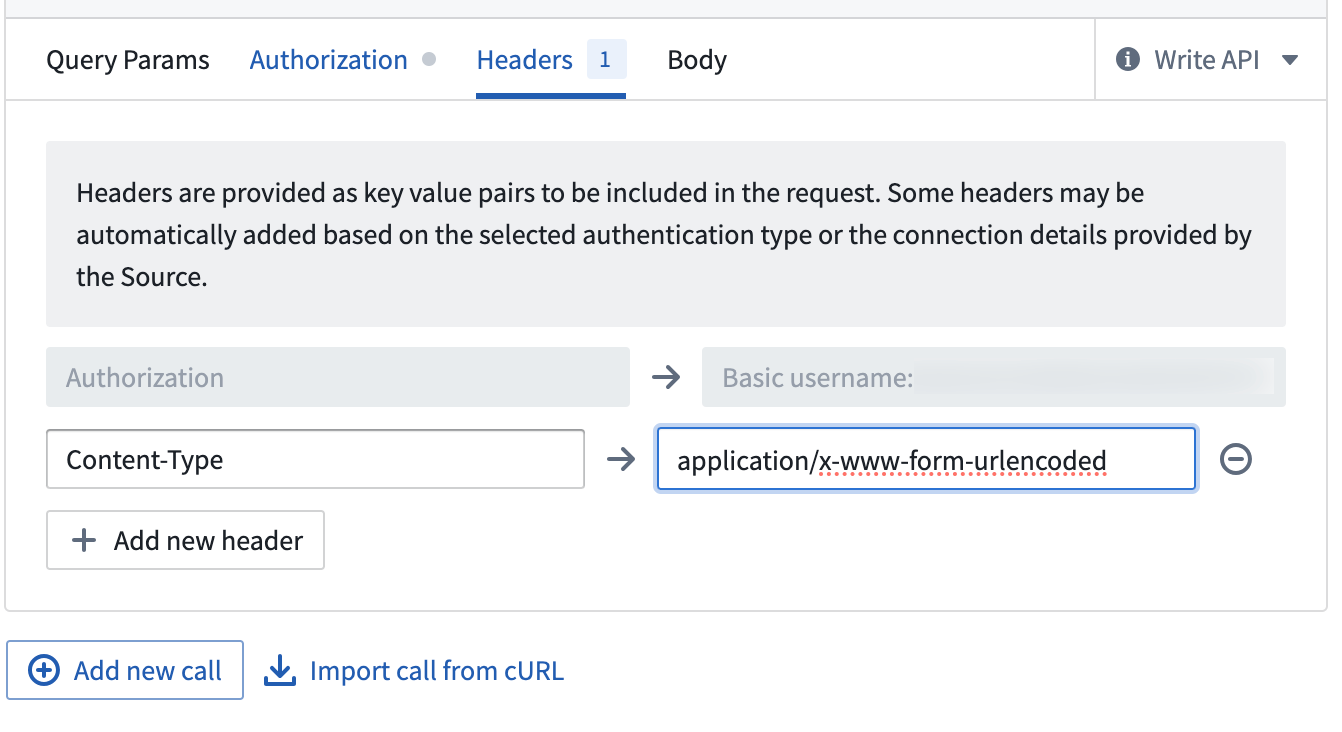
sap-clientas a Query Param if needed. - On the Headers tab, add the following header:
Content-Type→application/x-www-form-urlencoded
- Set up these two Input Parameters (both strings):
client_idrefresh_token
- Then under the Body tab, add these three entries:
grant_type→refresh_tokenclient_id→ Mapped to theclient_idinput parameterrefresh_token→ Mapped to therefresh_tokeninput parameter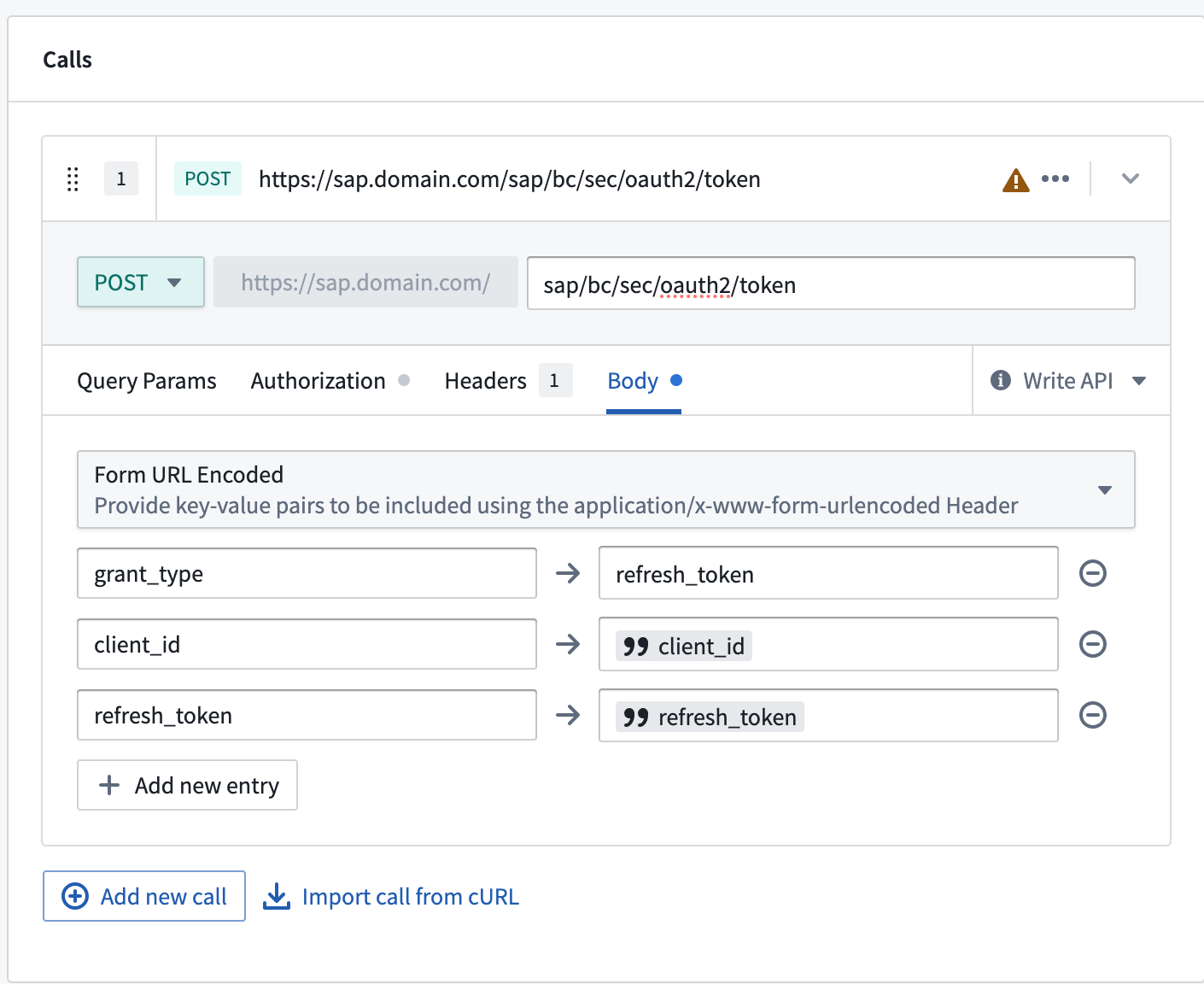
- Create exactly the same five Output Parameters as for the authorization code flow webhook. All should be of type string and should be extracted by key from the response.
access_tokentoken_typeexpires_inrefresh_tokenscope
- Save the webhook by selecting Create webhook and continue.
Outbound application setup
- Navigate to the Foundry Control Panel and select Outbound applications.
- Give the application a name then follow the steps outlined under Configuration options for on-premise OAuth servers.
- The two webhooks created earlier should be used as the Token webhook and Refresh token webhook respectively.
- The Authorization page URL should be of the form:
https://<SAP_DOMAIN>/sap/bc/sec/oauth2/authorize
- Under OAuth 2.0 settings, the Client ID should be set to the client ID from the SAP OAuth 2.0 server configuration. Under Scopes, add
/PALANTIR/SRV_0001. - Save the outbound application.
- This outbound application can now be used when creating an SAP webhook.