- Capabilities
- Getting started
- Architecture center
- Platform updates
Responding to global security incidents via an integrated alerting and triaging application
Industry Sector: Defense
Business Function: Security
Palantir Foundry’s Global Incident Response offering can improve an organization’s safety and security posture by rapidly implementing a unified, data-driven solution. This solution includes modules for risk scoring, incident triage, accounting for people, managing emergency communications, and understanding and analyzing actions taken. All these tools incorporate baked-in data and privacy protection components, and integrate seamlessly with existing tools, data feeds, and standard operating procedures (SOPs).
Challenge
In order to conduct incident response work effectively, security teams are usually forced to choose between an inflexible out-of-the-box system that claims to meet all their needs or custom building a global operations center out of various building blocks in an effort to retain ownership and flexibility.
Moreover, security teams at global organizations are inundated with data about emerging events in a chaotic world, and often struggle to separate signal from noise when trying to understand if or how events may affect the security of their people and assets. Then, when a response is necessary, it can be time consuming or even impossible to identify exactly who may be affected, due to the use of siloed systems used to manage and track different parts of the organization. And no matter how effective a given response is, there is no single source of truth that captures what decisions were made when, and who accessed what data for what purpose.
Solution
A global security team has built a comprehensive set of modules, scenarios, and models while retaining the flexibility and control needed to ensure they can meet changing requirements and not be locked in to a single vendor or system.
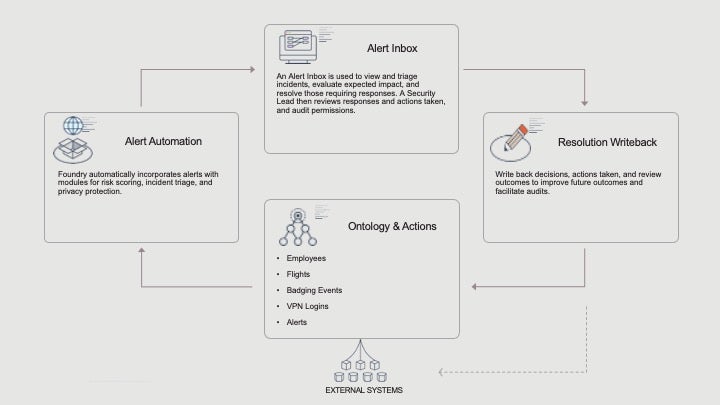
In terms of workflow solution, Foundry provides a data-driven operational framework for receiving, triaging, and actioning on security alerts.
A security operations analyst (user type) reviews an incident alert inbox to view and triage incidents based on their expected impact to business assets and respond to and resolve each incident requiring response.
A security lead reviews all incident responses and alert triage actions taken based on their time to respond, resolution achieved, and data accessed in the course of responding.
Users and stakeholders
- Security Operations (analysts, team leads, etc.)
Impact
The main KPIs to track for defining success of the use case are:
- Time to respond.
- Ratio of false positive incident alerts to Responses required.
- Time to resolution.
How it's made
The Global Incident Response solution includes modules for risk scoring, incident triage, accounting for people, managing emergency communications, and understanding and analyzing actions taken. All these tools incorporate baked-in data and privacy protection components, and integrate seamlessly with existing tools, data feeds, and SOPs.
Implement a similar use case
This use case implements the following Pattern. Follow the link below to read more about a particular Pattern and learn how it is implemented within Foundry.
- Alerting workflow (used for 7 other use cases)
Want more information on this use case? Looking to implement something similar? Get started with Palantir. ↗