Configure outbound applications with OAuth 2.0 authorization code grants
Outbound applications provide a way for administrators to manage OAuth 2.0 connections to external systems from workflows built in Foundry. Outbound applications are managed at the Organization level in Control Panel.
An outbound application represents a bundle of configurations required for Foundry to behave as an OAuth 2.0 client. The application makes requests to another system that can behave as an OAuth 2.0 server.
Outbound applications in Foundry only support the OAuth 2.0 authorization code grant ↗ type. To set up an OAuth 2.0 client credentials grant, follow these resources to manually establish the handshake process within a webhook.
Create an outbound application
To create an outbound application, first navigate to the Outbound applications in Control Panel, under Organization settings. If you have access to multiple Organizations, be sure to select the Organization in which you wish to create your outbound application. All users of this Organization with permission to set up sources in Data Connection will be able to select any outbound application as an authorization mechanism for their connection.
To view the Outbound applications page, you need access to the "Manage outbound applications" workflow, which is granted by default to the Organization administrator role in Control Panel.
Learn more about configuring roles.
Select New application and provide the required inputs to set up your outbound application. Detailed configuration options are listed below.
Configuration options
The following configuration options apply to both cloud-based and on-premise OAuth 2.0 servers.
| Option | Required? | Description |
|---|---|---|
| Application name | Yes | A user-facing name for this outbound application. The name is visible when selecting the outbound application in Data Connection while configuring authentication for a source. |
| Description | No | A description of the outbound application. |
| Approval prompt | Yes | This text will be displayed when using the authorization grant flow before opening a pop-up window to display the login prompt for the external OAuth 2.0 provider. |
| Client ID | Yes | The client identifier ↗ from the OAuth 2.0 provider. Note that some external systems may use a different term to refer to client ID. |
| Client secret | Yes | The client secret ↗ from the OAuth 2.0 provider. Note that some external systems may use a different term to refer to a client secret. |
| Scopes | Yes | The list of scopes configured in on the OAuth 2.0 server corresponding to the provided client ID. The list entered here must match what is listed in the administration interface for the external system. Scopes may be left blank to indicate that an empty list of scopes should be provided when authorizing with the OAuth 2.0 server. |
| Access token expiration | No | An optional access token expiration. Normally, this value is returned by the OAuth 2.0 server as part of the authorization grant flow. Any value entered here will be ignored if the server provides an access token expiration. |
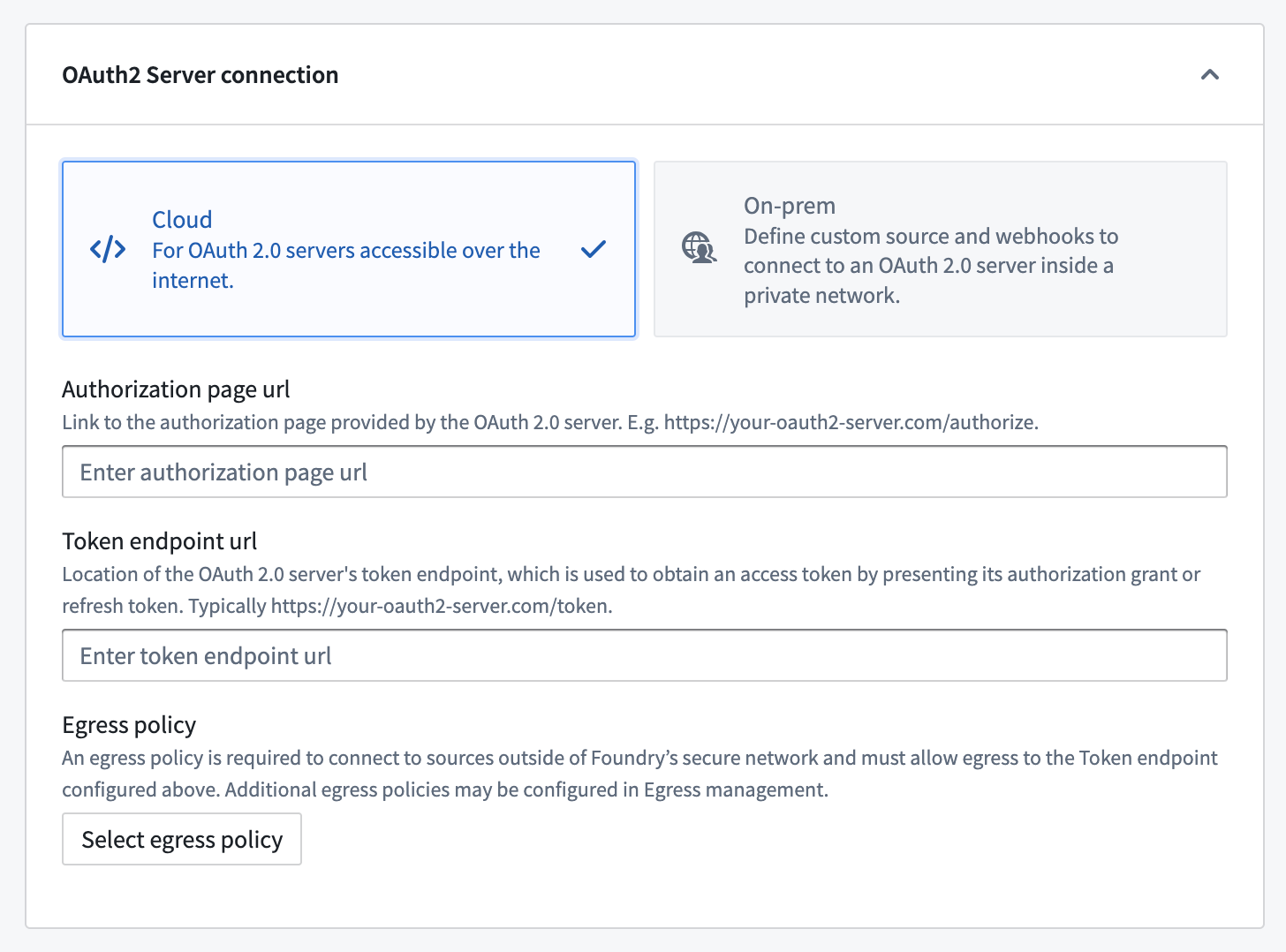
Configuration options for OAuth servers reachable from Foundry's network directly
We recommend using a direct connection when setting up an outbound connection if the OAuth 2.0 server is reachable from Foundry directly. For cloud-hosted Foundry instances, this means a server that can be reached through a direct Internet connection.
| Option | Required? | Description |
|---|---|---|
| Authorization page URL | Yes | The authorization endpoint ↗ for the OAuth 2.0 provider. Generally, this URL is similar to https://oauth2-server.com/authorize and should be available in public documentation for most SaaS offerings. |
| Token endpoint URL | Yes | The token endpoint ↗ for the OAuth 2.0 provider. Generally, this URL is similar to https://oauth2-server.com/token and should be available in public documentation for most SaaS offerings. |
| Egress policy | Yes | To connect directly to the OAuth 2.0 server, you must create and attach an egress policy that allows connecting to the token endpoint URL. Egress is managed per enrollment. |
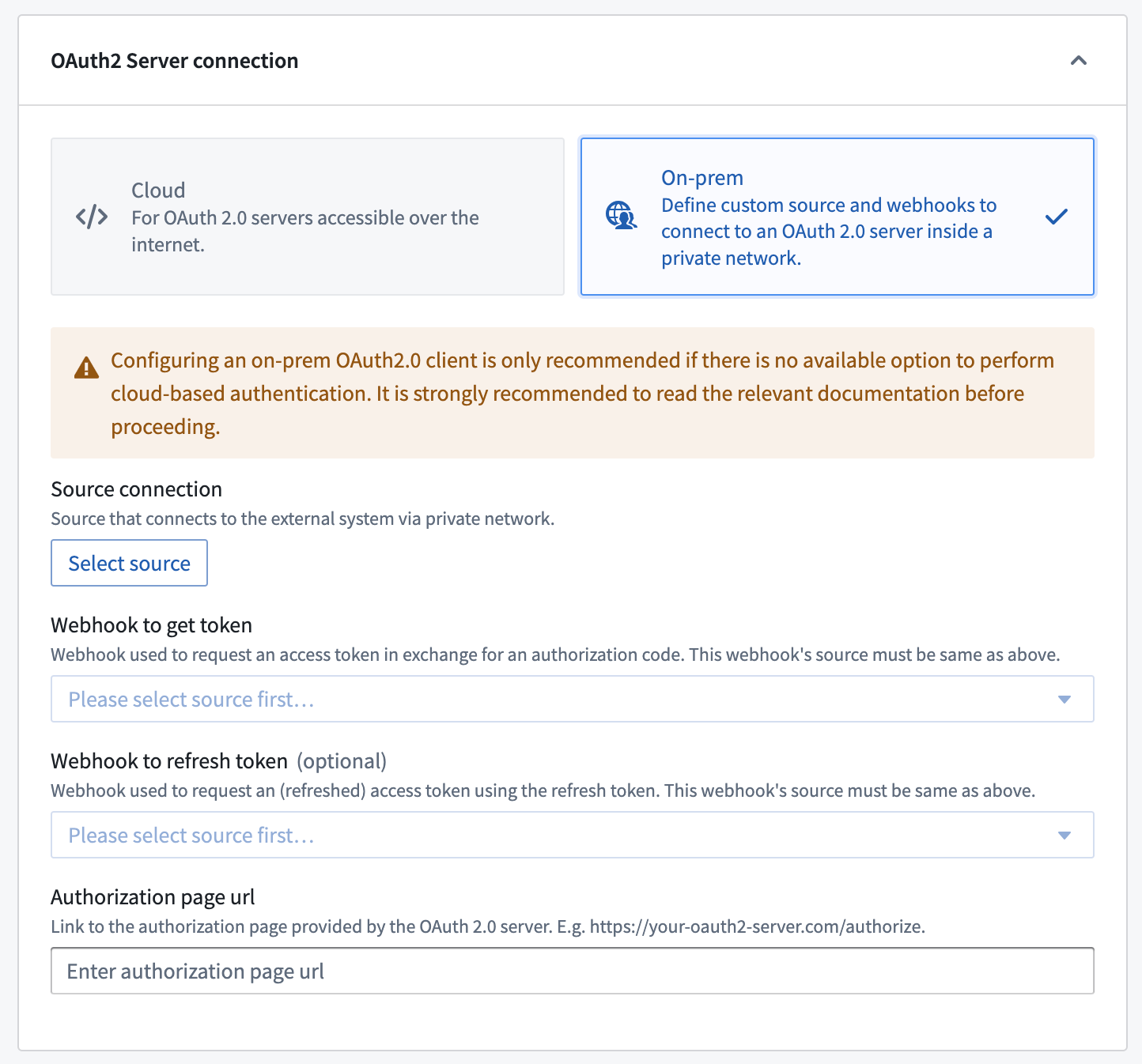
Configuration options for OAuth servers on a network different from Foundry's network
On-premise configuration should only be used if the OAuth server is inside a private network and cannot be reached with a direct connection egress policy.
| Option | Required? | Description |
|---|---|---|
| Source connection | Yes | Choose a REST API source that is configured to use an agent worker to connect to the OAuth 2.0 server inside your network. |
| Webhook to get token | Yes | A webhook that calls the token endpoint ↗ for the OAuth 2.0 server to fetch a token. See the section below for more information. |
| Webhook to get refresh token | No | A webhook that calls the token endpoint ↗ for the OAuth 2.0 server to refresh a token. See the section below for more information. |
| Authorization page URL | Yes | The authorization endpoint ↗ for the OAuth 2.0 provider. Generally, this URL is similar to https://oauth2-server.com/authorize. |
Connect to an OAuth 2.0 server inside a private network
When OAuth 2.0 servers are not exposed to the open Internet, OAuth 2.0 handshake requests must be routed through a custom REST API source using an agent worker to connect to the server. This method requires you to write your own requests that will be used to perform the OAuth 2.0 handshake.
The first step is to create a REST API source that can connect to your OAuth2 server. For example, you might configure your source with a domain and client secret:
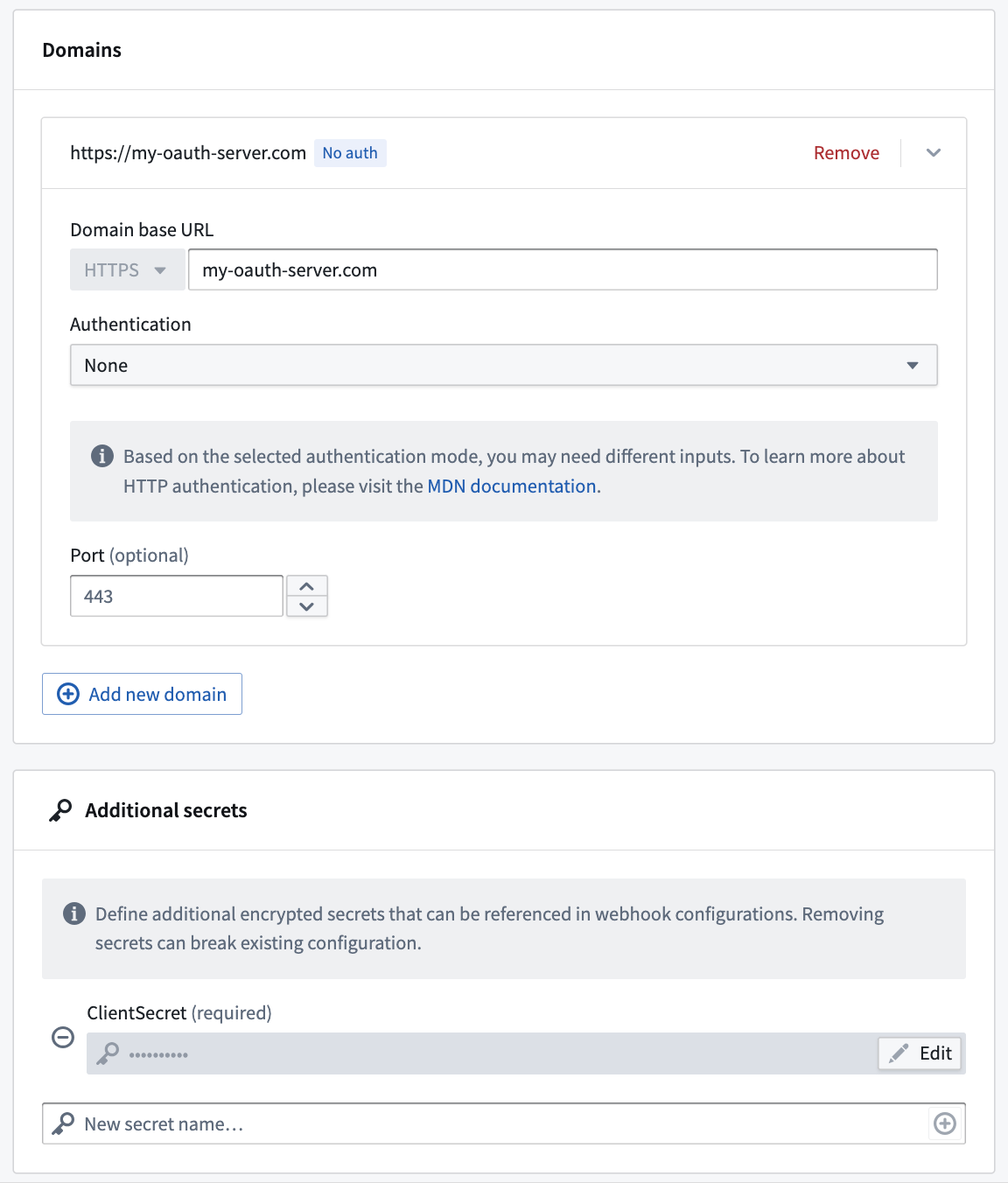
Next, you need to create a webhook on that REST API source that can call the /token endpoint of the OAuth 2.0 server. You can optionally create a second webhook that can refresh the token.
The example below shows an example of an OAuth 2.0 handshake request to a hypothetical OAuth 2.0 server using cURL:
curl -XPOST 'https://<oauth-server>/token'
-H 'Content-Type: application/json'
-d '{"client_id":"8b3df622e71449519cd9b0160b9e39f7", \
"client_secret":"04011f337b984df0ad8c58a50f9e91f5", \
"code":"a8ec5e83728e480fa6bfda4eb8e122a3"}'
An example response could look like following:
{ "access_token":"1846149cf5774c3d8eaeb18b75f7178d",
"refresh_token": "1846149cf5774c3d8eaeb18b75f7178d",
"token_type":"bearer",
"scope":"<comma-delimited-set-of-scopes>",
"expires_in": "3600" }
As another example, a typical refresh request could look like the following:
curl -XPOST 'https://<oauth-server>/refresh_token'
-H 'Content-Type: application/json'
-d '{"client_id":"8b3df622e71449519cd9b0160b9e39f7", \
"client_secret":"04011f337b984df0ad8c58a50f9e91f5", \
"refresh_token":"a8ec5e83728e480fa6bfda4eb8e122a3"}'
The response would be identical to the handshake response above:
{ "access_token":"1846149cf5774c3d8eaeb18b75f7178d",
"refresh_token": "1846149cf5774c3d8eaeb18b75f7178d",
"token_type":"bearer",
"scope":"session",
"expires_in": "3600" }
Use the instructions in the next section to create the token and refresh token webhooks you will need to implement an OAuth 2.0 handshake in Foundry.
Token webhook
The token webhook should implement a request to the /token endpoint on the OAuth 2.0 server to fetch a valid token given a client_id, redirect_uri, and authorization_code. The token webhook must have the input and output parameters listed below. Learn more about webhook parameters.
Below is an example request configuration showing a standard OAuth 2.0 server token request:
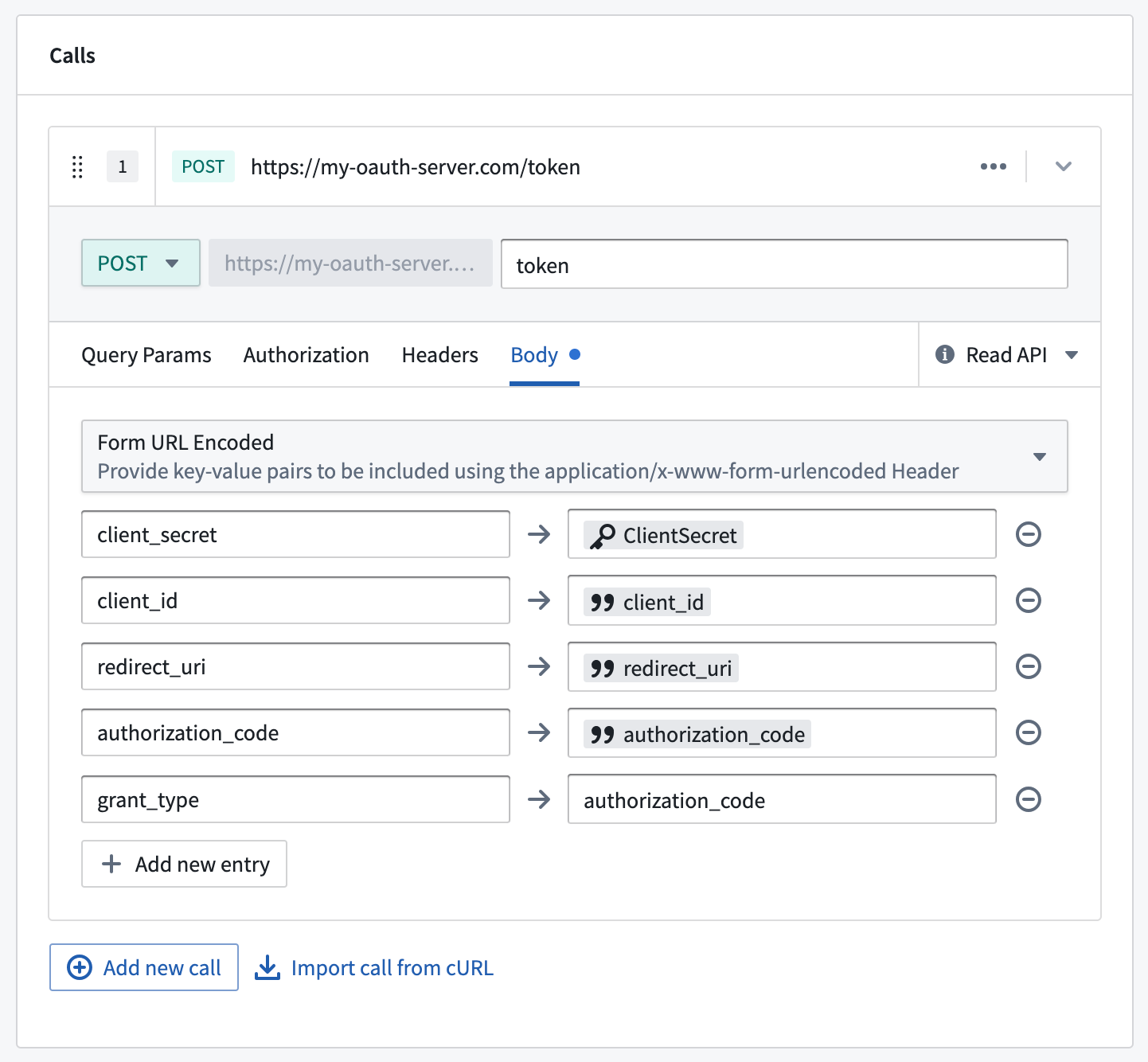
| Input parameter | Required? | Type |
|---|---|---|
client_id | Yes | String |
redirect_uri | Yes | String |
authorization_code | Yes | String |
You must also set grant_type=authorization_code as one of the entries in the webhook form body. Review the documentation for your OAuth 2.0 server for additional required configurations.
| Output parameter | Required? | Type | Comments |
|---|---|---|---|
access_token | Yes | String | |
scope | Yes | String | |
refresh_token | No | String | Not all OAuth 2.0 servers or applications will be configured to allow automatic token refresh. If no refresh token is returned, users will be prompted to re-authorize the application whenever the original token expires. |
expires_in | No | String | Not all OAuth 2.0 servers will return this parameter. If this parameter is not present or a value is not returned, the access token expiration in the outbound application will be used instead. |
Refresh token webhook
After creating the token webhook, you must create a second webhook for the refresh token flow using the input and output parameters listed below. The webhook should implement a request to the /token endpoint to fetch a new token given a refresh_token and client_id.
Below is an example request configuration showing a standard OAuth 2.0 server refresh request:
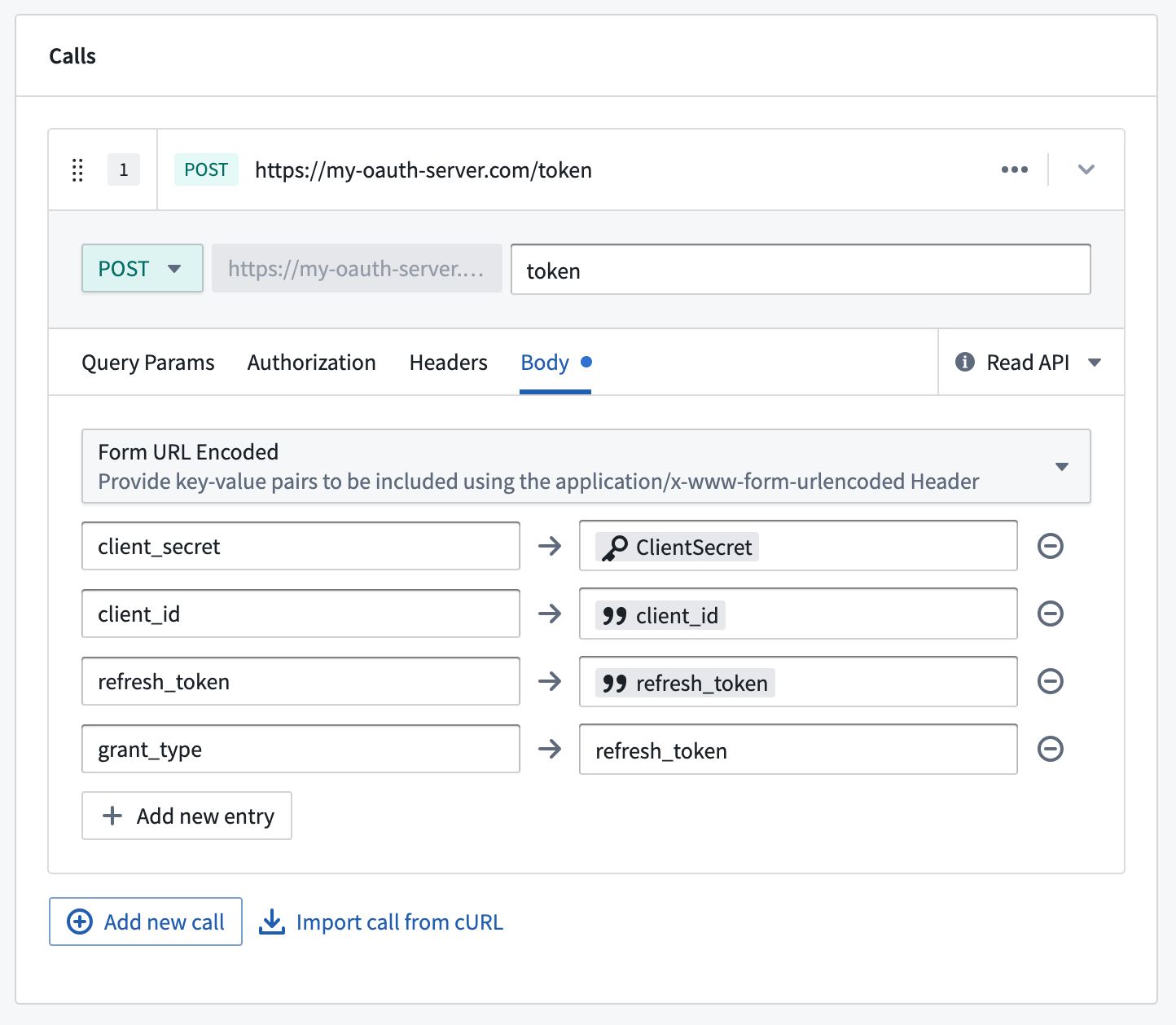
| Input parameter | Required? | Type |
|---|---|---|
client_id | Yes | String |
refresh_token | Yes | String |
You must also set grant_type=refresh_token as one of the entries in the webhook form body. Review the documentation for your OAuth 2.0 server for additional required configurations.
The available output parameters are the same as the parameters for the token webhook.
| Output parameter | Required? | Type | Comments |
|---|---|---|---|
access_token | Yes | String | |
scope | Yes | String | |
refresh_token | No | String | Not all oauth servers or applications will be configured to allow automatic token refresh. If no refresh token is returned, users will be prompted to re-authorize the application whenever the original token expires. |
expires_in | No | String | Not all OAuth 2.0 servers will return this parameter. If this parameter is not present or a value is not returned, the access token expiration in the outbound application will be used instead. |
Manage outbound applications
Once you create an outbound application, it will be available to all users in that Organization to use as the authorization method for a REST API source in Data Connection. The following options are available for administrators with permisssions to manage outbound applications.
Delete an outbound application
Deleting an outbound application will permanently remove stored tokens and refresh tokens for all users who have authorized the application. The application configuration, including the client secret, will also be permanently deleted. This action cannot be reversed.
Reset an outbound application
Resetting an outbound application will permanently remove stored tokens and refresh tokens for all users who have authorized the application. This effectively returns the application to the state just after initial setup when no user has yet completed the interactive authorization flow. The next time a user attempts to perform a workflow that requires a token from this outbound application, they will be prompted to complete the authorization flow again.
Enable an outbound application
Enabling an outbound application means that users may perform the interactive authorization flow to this external system. Disabling an application will prevent any previously stored tokens and refresh tokens from being used. However, these tokens will not be deleted and may be used again after the application has been re-enabled.
New users who have not previously authorized the application will not be able to perform the interactive authorization flow while the outbound application is disabled.
Newly created applications will be enabled by default and may only be disabled after being created.
Use outbound applications in Data Connection
Outbound applications may not always be compatible with automation workflows. If a user has already authorized an outbound application and a valid and unexpired token or refresh token is available, webhooks and Actions may run without issue. The interactive prompt is not supported through all clients, and OAuth 2.0 is not currently recommended for workflows run through automation or the Foundry API.
Outbound applications do not support usage by users from multiple Organizations. If users in multiple organizations need to authorize against the same OAuth 2.0 server, you must create a separate outbound application with a different REST API source for users in each Organization.
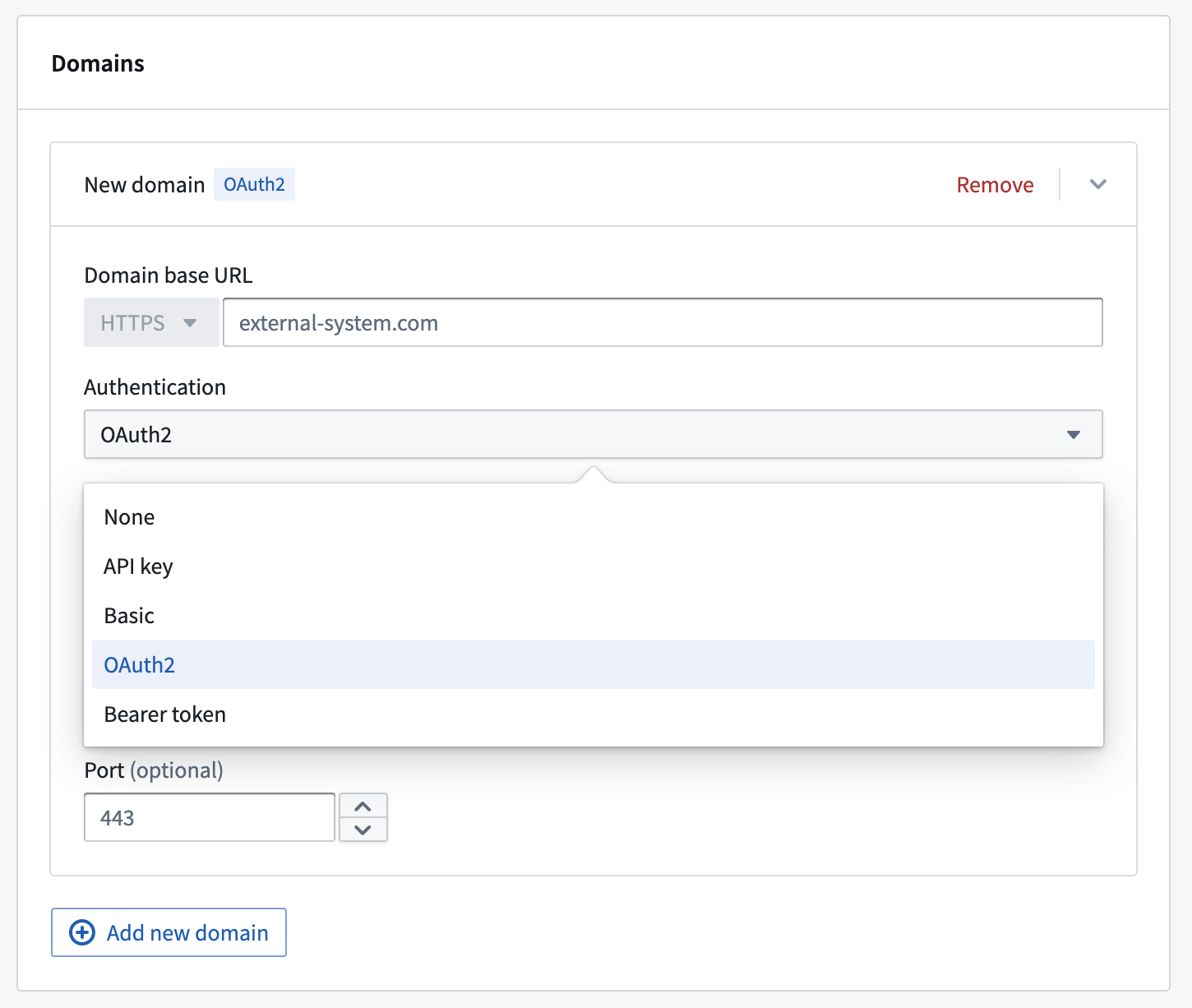
Once an outbound application is created and enabled, it may be used as the authentication method for a domain in a REST API source. When configuring a domain, select OAuth 2.0 and then select the desired outbound application from the dropdown.
Any webhooks using a domain with OAuth 2.0 configured will result in an interactive prompt for each user the first time they attempt to run it. Webhooks are most often invoked through Actions from Workshop; in this case, when running an Action in Workshop, the user will see a pop-up window showing the authentication page of the OAuth 2.0 server, prompting them to authorize Foundry to interact with this system on their behalf.
In order to call OAuth 2.0 backed webhooks in a Function-backed Action, navigate to the rules configuration page of your Action and call the webhook directly as the first rule followed by a Function to process the webhook response. You can also configure the webhook call to take inputs from a function.
If a token refresh workflow is configured, users are unlikely to see this prompt again unless the authorization is revoked in the external system or the outbound application is reset. If no refresh workflow is configured, the end user will see the authentication pop-up anytime the resulting token expires. Tokens often expire within minutes or hours, and we encourage use of the refresh flow for a better user experience.