What's new
2026-02-10
Latest changes
- Improvement - Apollo CLI version 0.647.0 includes a new
release-channel diffcommand that allows you to compare Releases between two Release Channels for Products in a specific Environment. This command shows which Product Releases exist on the source channel but not on the target channel. This is useful for identifying Releases that need to be promoted from one channel to another. To do this, run the following command:apollo-cli release-channel diff <environment-id> -s <source-channel> -T <target-channel>. Flags:--source-channelor-S(required): Source Release Channel to compare from.--target-channelor-T(required): Target Release Channel to compare against.--all: Show all Products including those already up to date.
- Improvement - You can now add a Default Channel column to the Environments table in Apollo. This column displays the default Release Channel associated with each Environment. The column is sortable and persists across page refreshes once added.
2026-02-04
Latest changes
- Improvement - Apollo CLI version 0.637.0 supports an
--image-prepull-config-timeoutflag that allows you to configure the timeout duration for pre-pulling container images. This gives you more control over the image preparation process during deployments.
2026-02-02
Latest changes
- Improvement - Apollo CLI version 0.631.0 includes new commands to provide bundle generation and Product Release management capabilities. The new commands include:
Release Channel commands:
release-channel export: Export all Product Releases from a Release Channel to YAML.release-channel import: Import Product Releases from a YAML file to a Release Channel.release-channel populate: Populate a Release Channel with releases from an Environment.
Entity commands:
entity compare: Compare Entity versions with latest available on Release Channels.entity sync: Fetch, transform, and merge Entity data from all Apollo Environments.
2026-01-29
Latest changes
- Improvement - Apollo now checks artifact availability in Artifact Registries before executing a Plan. When viewing a Plan, you can view which artifacts are available, which are unavailable, and which could not be checked. This can prevent Plan failures due to missing artifacts.
2026-01-28
Latest changes
- Improvement - Apollo CLI version 0.629.0 supports opening debug shells in Apollo environments directly from your local terminal using the command
apollo-cli terminal <environment-id>. This feature provides an interactive shell with pre-configured kubectl, enabling direct debugging and exploration without needing to use the web UI.
2026-01-27
Latest changes
- Improvement - You can now edit role policies for individual terminal profiles in Apollo. This allows you to manage access permissions at the profile level, providing more granular control over who can use specific terminal configurations.
2026-01-16
Latest changes
- Improvement - Apollo CLI version 0.623.0 supports bulk operations for product promotion management. The new
product promotion appendcommand allows you to append promotion pipeline stages from a template to existing pipelines. Both theappendandsetcommands now support a bulk mode via the--environmentflag to target all Products in an Environment simultaneously. Additional features include conflict detection with interactive resolution, automatic override with the--yesflag, and preview capabilities with the--dry-runoption.
2026-01-15
Latest changes
- Improvement - Apollo CLI version 0.622.0 supports multiple configuration profiles, allowing you to easily manage and switch between different Apollo environments. Similar to AWS CLI profiles or kubectl contexts, this feature includes new commands for creating, listing, showing, and switching between profiles. You can also import and export profiles to share configurations between machines. The CLI supports profile selection via command-line flags, environment variables, or configuration files.
2026-01-13
Latest changes
- Improvement - When creating terminal profiles in Apollo, you can now select which Artifact Registry to use. For Apollo Container Registry (ACR), a dropdown of available container images is provided. For other registries, you can manually enter the image name and version. Terminal profile details now include a link to the associated Artifact Registry.
- Improvement - You can now view and manage Artifact Registries across multiple spaces in Apollo. The Artifact Registries inbox displays registries from all spaces, with the ability to filter by organization. When creating a new registry, you can select which organization it belongs to.
2026-01-09
Latest changes
- Improvement - Apollo now provides direct links from mirrored configurations to their source Hub. When viewing a mirrored configuration, you can select the link to navigate to the exact same tab in the source Hub. Additionally, the View rendered config action is now disabled for mirrored configurations to reflect their read-only status.
- Improvement - Entity pages in Apollo now display status pills that show the reported or declared state source of the Environment the Entity belongs to. These pills provide visibility into the Entity's Environment status and include links back to the Environment page for further details.
2026-01-08
Latest changes
- Improvement - As of version 0.604.0, the Apollo CLI now includes commands for managing Product promotion pipelines. You can use the new
product promotion get,product promotion set,product promotion enable, andproduct promotion disablecommands to view and configure promotion pipelines directly from the command line interface.
2026-01-06
Latest changes
- Improvement - Apollo CLI version v0.596.0 has removed the experimental
module migratecommand, which was previously used to transition from the legacy Module definition format. This command was deprecated in November.
2026-01-05
Latest changes
- Fix - Failed Plan notifications now include a direct link to the Plans table with the relevant Plan selected. This improves navigation consistency with existing workflows in the Plans tab.
2025-12-19
Latest changes
- Improvement - Apollo CLI version 0.587.0 now supports Release Channel commands, allowing you to manage and interact with Release Channels directly from the command line interface. This addition expands the CLI's capabilities for Product Release management.
2025-12-18
Latest changes
- Improvement - Apollo CLI version 0.585.0 now supports an optional
--only-summary=falseflag for theentity listcommand. When this flag is set to false, the command outputs detailed entity declared state information including Product ID, Release Channel, versions, maintenance windows, and other configuration details. The default value istrue, which maintains the existing summary output behavior.
2025-12-11
Latest changes
- Improvement - Apollo now displays a callout in the health inbox panel for relayed Entities. This callout provides a direct link to the Entity's health inbox in the other Hub, maintaining the same time selection for seamless navigation between related health information.
2025-12-10
Latest changes
- Improvement - Apollo now provides a direct link from the external dependencies constraints to the Environment's external dependencies configuration. This makes it easier to navigate between constraint messages and the source configuration that defines those constraints.
- Improvement - Administrators can now delete import Pipelines by selecting the Pipeline from the Import History tab. Select Delete Pipeline from the Actions dropdown of the import Pipeline. When selected, a confirmation modal appears that requires you to enter the Pipeline name before deletion is completed.
- Improvement - You can now view the reason why a Release Channel promotion was canceled directly in the promotion graph. This provides visibility into why promotions were stopped, such as Releases being recalled or issues with canaries.
- Improvement - Apollo now clearly indicates that timed promotion evaluations do not include weekends. This information is displayed when configuring timed promotion stages and is available in tooltips when viewing existing timed promotion configurations in Release Channels.
2025-12-05
Latest changes
- Improvement - Comments and field reordering are now recognized as valid changes to configuration blocks. Previously, when you added comments or reordered fields in the newest version block, you would still receive a warning about not making changes to the latest config block. This improvement ensures that all types of edits to the newest version block are properly recognized.
- Improvement - Team management operations in Apollo now use role-based access control (RBAC) exclusively, eliminating the need for change requests. Users with appropriate permissions can create, update, or delete teams directly in their Apollo Hub.
- Improvement - The Bundle Advisories section in Export is now expandable. This makes viewing long advisory information easier and allows you to collapse the advisories when not in use.
- Improvement - When installing a Product onto an Environment in Apollo, the Environment selection dropdown now only displays authoritative Environments. Non-authoritative Environments, which cannot be used for installations, are no longer shown as options.
2025-12-02
Stagger Product upgrades with ramped rollouts
Ramped rollouts are now available on all Apollo Hubs, allowing you to stagger Product upgrades within a Release Channel. A ramped rollout is a rate-limiting mechanism that distributes Entity upgrades across a specified time window.
Ramped rollouts are useful for Products with a large number of Entities. Rather than upgrading all the Entities at once, ramped rollouts allow upgrades to happen gradually. This enables earlier detection of issues and reduces the risk of widespread incidents.

Diagram that shows how Product upgrades are staggered throughout the rollout window when ramped rollouts are used.
You can configure ramped rollouts in your Product's Upgrade settings. For each Release Channel in the promotion pipeline, you can define a rollout window over which upgrades should be distributed.
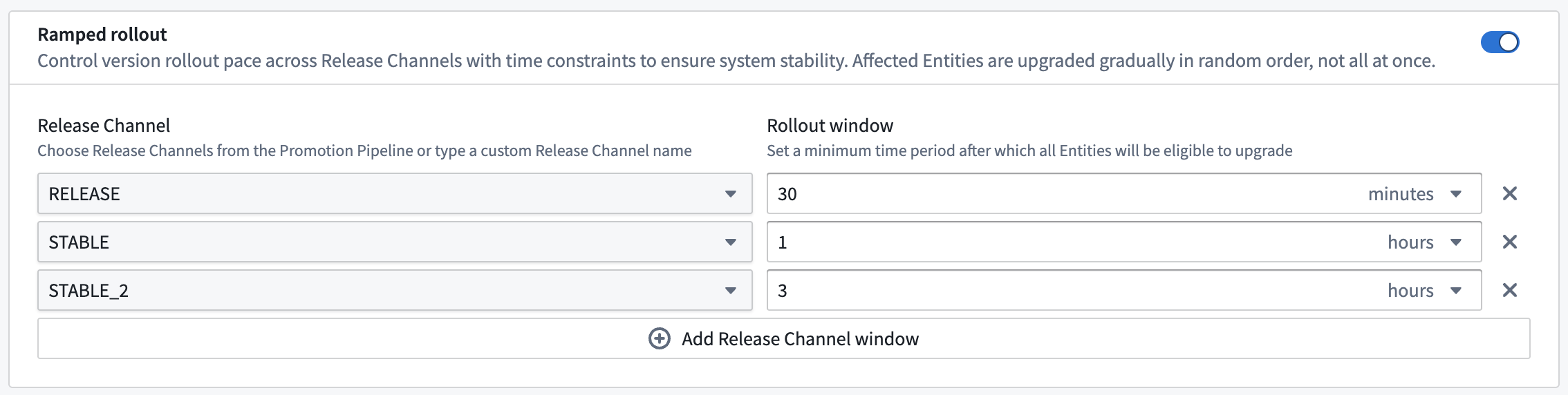
Example Product settings with ramped rollouts configured.
Learn more about ramped rollouts.
Other changes
- Fix - Filters in the vulnerability scan findings panel now work correctly. When multiple filters are selected, any finding that matches any of the selected filters will be included in the results.
2025-11-26
Latest changes
- Improvement - Schema compatibility checks for assets are no longer performed when issuing install commands. This removes irrelevant warning messages that were previously displayed when working with assets.
- Improvement - Data selection rules are now listed in a nested dropdown menu when creating an export pipeline. Rules are organized into categories of 'by resource' or 'by label', making it easier to find and select from a larger number of available rules. The dropdown also includes search functionality to quickly filter rules within each category.
2025-11-25
Latest changes
-
Improvement - Labels now consistently use the pill-shaped icon throughout the interface. Additionally, the Product icon is now correctly displayed in the pipeline export Product rule dropdown.
-
Improvement - Apollo now displays role change history for role-based access control (RBAC) changes. You can view who made changes to roles for Environments, Products, Pipelines, and other resources.
-
Improvement - You can now filter resources by labels when configuring export pipelines in Apollo. This new capability allows you to select Environments and other resources based on their labels rather than choosing specific resources individually. When new resources are assigned matching labels, they are automatically included in existing pipelines without requiring updates to the pipeline configuration.
2025-11-21
Latest changes
- Improvement - As of version 0.571.0, Apollo CLI no longer supports the legacy composite Module definition format. You can use the
apollo-cli module migratecommand to transition your existing Modules to the current format. - Improvement - Apollo now displays the total terminal latency as well as the latency between you, the Spoke, and the Hub. This replaces the previous text-only display, providing a clearer representation of terminal connection performance.
- Improvement - Environment role management has been moved from the Environment management settings dialog to a dedicated dialog in Apollo. This change provides a more focused interface for managing RBAC for your Environments. You can access this functionality from both the Environment details panel and the Environment Roles table.
2025-11-19
Latest changes
- Improvement - Apollo now displays more detailed information about invalid dependencies. When viewing invalid dependencies, you can now view both the current version and the required version for each Entity, making it easier to identify and resolve version conflicts.
2025-11-18
Latest changes
- Improvement - Apollo no longer displays the deprecated field that indicated if an Environment is remote. This field was no longer relevant to current functionality and has been removed from the interface.
- Improvement - Apollo now displays only the relevant details for Helm chart Plans instead of the entire JSON object. This change makes it easier to view and understand the important information in Plans by showing only the contents of the details field in the expandable code block.
- Improvement - Apollo now includes a direct link to the GraphQL API explorer (GraphiQL) in the sidebar navigation. This makes it easier to access and discover the API explorer without having to manually edit the URL.
2025-11-17
Latest changes
- Improvement - Apollo CLI version 0.568.0 adds support for the Helm
resource-readiness-timeoutmanifest extension flag. This new configuration option allows you to specify custom timeout values for Helm resources to reach ready state during deployments.
2025-11-14
Latest changes
- Improvement - The apollo-cli module evaluate command now provides clearer documentation and more helpful error messages about valid values for the
--featureflag. When using this command, users will now receive specific guidance on which feature options are supported. - Improvement - The remote Environment label has been removed from the Environment page. This change streamlines the Environment view by eliminating outdated terminology that was no longer accurate for different connection statuses and edit sources.
2025-11-06
Manage Kubernetes namespaces directly in Apollo
Environments editors can now manage their Kubernetes namespaces directly in Apollo for their Environments. This feature gives you full control over namespace lifecycle management through Apollo's interface.
You can create a namespace in the K8s Namespaces section of your Environment's Settings tab. Select New K8s Namespace.
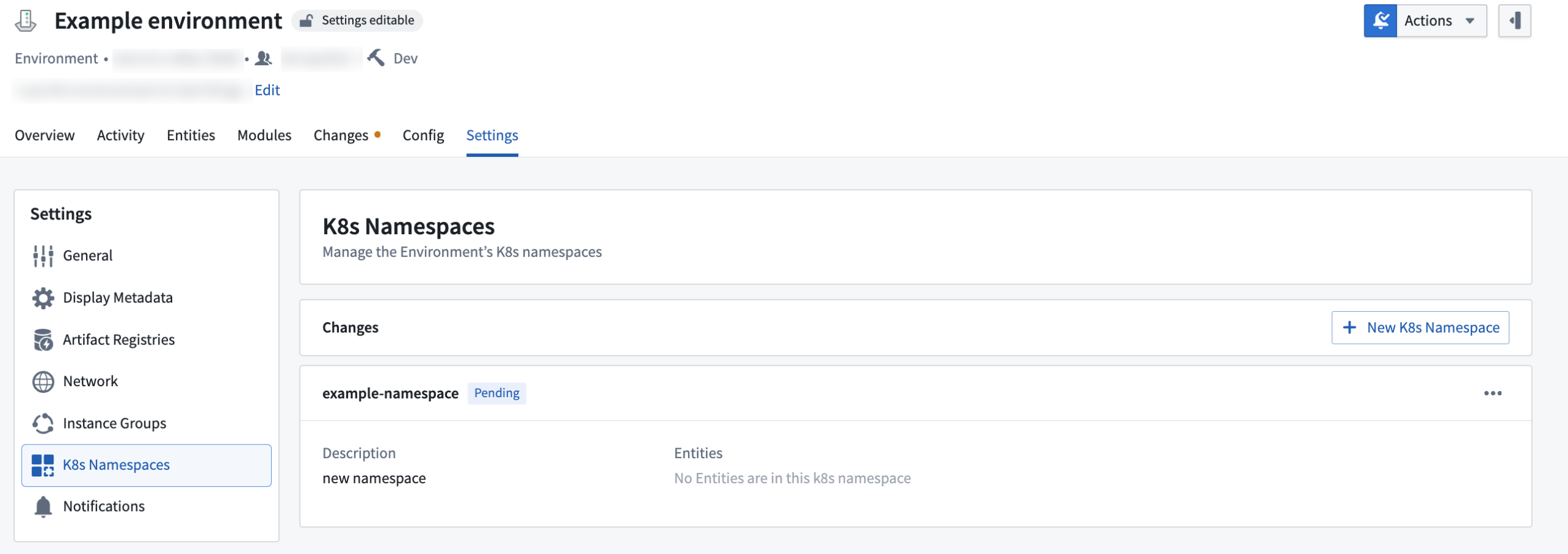
An example Environment with a namespace created.
Once a namespace is created, you can install Entities in that namespace. When installing an Entity in the Environment, you can select a Kubernetes namespace from the K8s namespace dropdown.
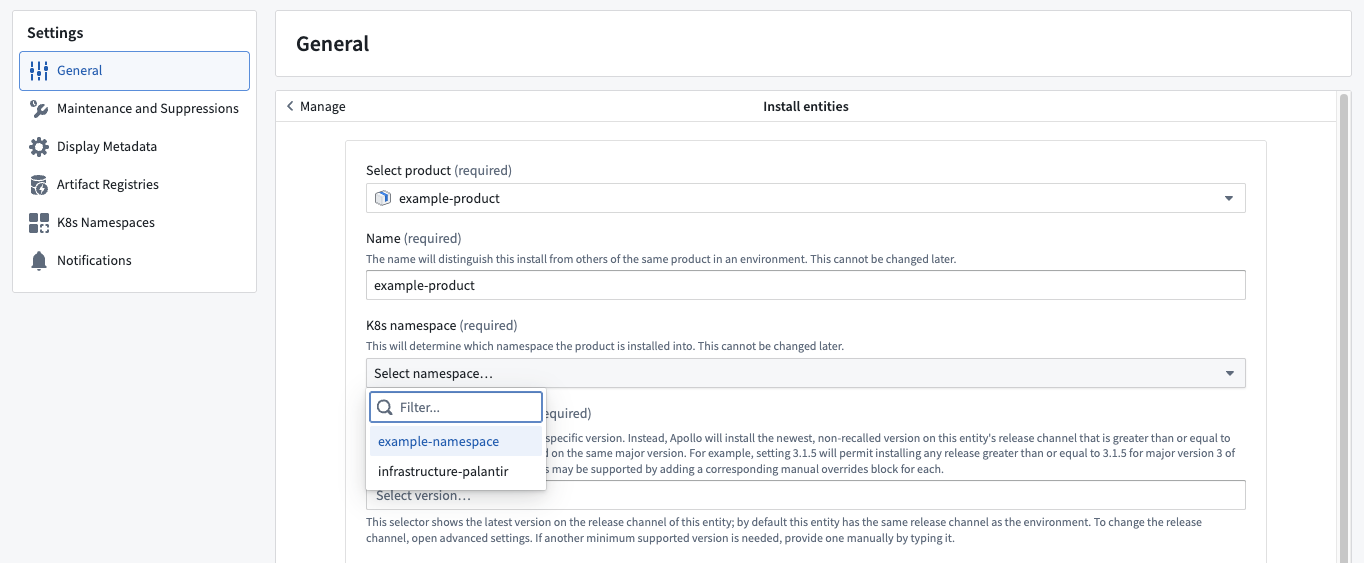
Select a namespace from the K8s namespace dropdown.
Learn more about managing Kubernetes namespaces.
2025-11-04
Latest changes
- Improvement - You can now search for Entities in Apollo using their resource identifiers (RIDs). When you enter an Entity RID in the search bar, Apollo will display the matching Entity in the search results, allowing you to navigate directly to it.
2025-11-03
Latest changes
- Improvement - Terminal latency information is now displayed in the top-right corner of open terminal sessions. You can hover over the latency indicator to view detailed client and Spoke latency times. These metrics update automatically every five seconds, providing real-time feedback on connection performance.
2025-10-30
Latest changes
- Improvement - Apollo now displays External Palantir Build as an Artifact Registry type. Similar to other registry types, this registry type is visible in the Artifact Registries Hub settings, but cannot be created or have its credentials edited through the Apollo interface.
2025-10-28
Latest changes
- Improvement - Apollo now validates policy compliance when adding or removing labels on resources. When you modify labels on a single resource, Apollo performs a dry run validation to ensure the changes meet established policies before applying them.
2025-10-23
Latest changes
- Improvement - Apollo CLI version 0.550.0 introduces new configuration options for both the Release Channel and page size when listing Product Releases. The default Release Channel is
RELEASE, and the default page size is 100. This improvement provides more flexibility when querying Product Releases.
2025-10-22
Latest changes
- Improvement - Product settings are now organized into separate tabs for general settings and upgrade settings. This change provides a more structured interface for managing different aspects of your Products. Upgrade-specific settings such as background configurations, soak times, and maintenance windows are now managed in a dedicated tab.
2025-10-10
Latest changes
- Improvement - Apollo now uses role-based access control (RBAC) for team management operations. Users with appropriate permissions can create, update, or delete teams directly without requiring change requests to be approved.
- Improvement - The Terminals tab now provides dedicated list view for terminal sessions in Environments. You can view all terminal sessions, create new sessions, and delete sessions. The Terminal sessions list also supports column sorting to help manage multiple sessions.
2025-10-06
Latest changes
- Improvement - Apollo now displays upgrade batch information for Entities and Product Releases that are assets. This information appears in the Details panel and Overview pages, making it easier to identify which batch to upgrade Releases in. The upgrade batch field is only shown for assets that have this property configured.
2025-10-02
Other changes
- Improvement - Apollo now provides Hub export settings that allow you to customize the metadata of a Hub for export. You can specify the display name and control exportability settings using the new Import & Export tab in your Hub settings.
- Improvement - Users can now select the connection settings when creating a new Environment in Apollo. This determines whether agents in the Environment will connect directly to the current Hub or to another Hub.
- Improvement - Apollo now displays a settings tag that indicates whether Environment settings are editable in the current Hub or a different one. Select this tag to switch the edit source for Environment settings.
- Improvement - Module preset variables are now displayed in multiple locations throughout your Apollo Hub. You can view Module variables in the overview page, details panel, content inbox, and installed Module details. When installing or updating Modules, you can configure preset variables with a preview that reflects changes. Module variable configurations are also visible in change requests.
- Improvement - Apollo now displays the current tag in Environment edit source and connection settings dialogs. The Hub link has been improved to direct users to the specific Environment in the other Hub. When a Hub is not known, it will display as "Unknown Hub" instead of "Another Hub". Warning messages for edit source have also been updated to provide clearer guidance.
- Improvement - Apollo now provides a streamlined interface for no-source, undetermined, and relayed Entities. The Entity overview for these types no longer displays installation status tags, plans, node health widgets, or status fields. Related tabs such as activity, health, monitors, resources, and security have been removed. Entity actions like Mute and manage secrets are disabled with explanatory tooltips. In the Modules view, these Entities display only count information without status indicators.
- Improvement - A warning callout is now displayed when an Environment has undetermined reported state, providing clearer visibility into connection issues. Additionally, the Environment agent status tag has been updated to reflect the reported state source. Users can now access connection settings directly from the connection status tag for more efficient troubleshooting.
- Improvement - Callouts are now displayed for Environments with mirrored declared state source in read-only mode. When an Environment has this source type, users cannot edit configurations in the current Hub. Actions such as editing environment or entity configurations, modifying artifact registries, and installing or uninstalling modules are disabled.
- Improvement - Apollo now restricts certain Environment actions based on the reported state source. The manage secrets dialog is read-only when the reported state source is relayed. For Environments with agents reported state source, the config editability cannot be set to downstream. Additionally, some Environment actions such as generate manifest and Environment setup steps are disabled based on the reported state source.
- Improvement - Apollo now provides direct links to recalls in notifications for open-ended recalls. When you receive a notification about an open-ended recall, you can select the link to navigate directly to the recall details.
-
- Improvement - Apollo CLI version 0.518.0 adds supports an
--ignore-recallsflag for the Module install command. This allows you to proceed with a Module installation even if all Releases of a Product are recalled.
- Improvement - Apollo CLI version 0.518.0 adds supports an
- Improvement - Apollo CLI version 0.519.0 provides an
--ignore-secret-requirementsflag for installing or updating Modules. This allows a Module installation or update to proceed even if the secrets the Module requires have not been set, giving users more flexibility in Module management workflows. -
- Improvement - Apollo CLI version 0.524.0 introduces improvements to the help text for Apollo CLI publish commands. The help text now more clearly explains what each command does, making it easier to understand which command to use for specific needs.
- Improvement - Apollo CLI version 0.531.0 allows users to specify a space ID in various Apollo CLI commands. This enhancement allows guest users to work with spaces they have access to, even if they are not part of the primary organization that owns the space. Commands that now support space ID specification include product-release create, product-release asset publish, and several others.
- Improvement - Apollo now uses role-based access control (RBAC) for team management operations. Users with appropriate permissions can create, update, or delete teams directly without requiring change requests to be approved.
2025-09-18
Introducing Environment edit source
Environment editors can now configure the edit source for an Environment. The edit source determines where the Environment's settings can be modified.
Learn more about Environment edit source.
2025-09-17
Introducing Environment connection settings
Environment editors can now configure the connection settings for an Environment. Connection settings determine how Apollo handles agent connectivity for an Environment. This replaces the previous LOCAL and REMOTE Environment types which are being deprecated.
Learn more about Environment connection settings.
2025-09-16
Introducing Module preset variables
Preset variables allow you to define groups of related variables that are configured together. With preset variables, you can simplify Module configuration by defining presets for multiple variables and exposing them through an intuitive control. A common use case is resource profiles, where selecting a single profile option (like "small", "medium", or "large") automatically configures resources such as CPU and memory values for the target environment appropriately.
Learn more about preset variables.
2025-09-11
Other changes
- Improvement - Users can now sort the Entity status column in Apollo installations. The sort order prioritizes different statuses with blocked Entities appearing first, followed by temporarily blocked, ongoing changes, up to date, and not reported Entities. Both ascending and descending sort orders are supported.
- Improvement - Apollo now displays the dependency group field in the Entity details widget on the Overview page and in the Entity Details panel. This additional information helps users better understand Entity relationships and dependencies.
- Improvement - As of Apollo CLI version 500.0, users can now specify a space ID in the configure command. When provided, this space ID is prioritized over inferred spaces for various publishing commands including product-release create, product-release asset publish, and several deprecated commands. This enhancement is particularly useful for users who need to publish products to spaces not owned by their organization.
- Improvement - Apollo now allows users to switch the edit source of an Environment's settings between Hubs. Users with appropriate permissions can access this functionality through a new action in the Environment page, where they can select which Hub should manage the Environment's configuration and provide a rationale for the change.
- Improvement - Apollo now provides a multi-step workflow for editing the connection settings of an Environment. This workflow guides users through the process with a structured interface, making it easier to configure Environment connection settings.
- Improvement - Apollo now provides links to other Hubs when an Environment is controlled by another Hub. When viewing Environments, you can select the Hub link to navigate directly to the controlling Hub. If Hub metadata is not available, the Hub name will be displayed as text without a link. If no display name is set, it will show as "Another Hub".
- Improvement - Apollo now provides options to select the edit source for Environment settings in pipelines. When configuring Environment rules, users can choose between 'mirrored' and 'upstream' options for the target declared state source, providing more flexibility in how Environment configurations are managed.
2025-08-05
Dependency groups now support Product Release incompatibilities
Product Release incompatibilities are now supported for dependency groups. An Entity will only consider a Product Release incompatibility active if the Entity shares at least one group with the target Entity.
Other changes
- Improvement - Users can now edit a Module's product settings the same way as Products. Navigate to the Settings tab on a Module page to configure options such as contact teams.
- Improvement - Apollo now displays a warning when you attempt to edit an older version of an Entity config. The warning requires acknowledgment before proceeding with the edit, helping prevent unintentional modifications to outdated configurations.
- Improvement - The display name field has been removed from the team creation and update dialogs in Apollo. Team display names are now managed exclusively through the Edit action in the team Properties settings after team creation.
- Improvement - Module paths in Apollo now include space information in their URL structure, consistent with other resources like Environments and Products. This change supports working with Modules across different spaces in a Hub.
- Improvement - Apollo now uses Maven coordinates instead of Module IDs. When accessing a Module using a Module ID, you will be automatically redirected to the appropriate URL with the Module coordinate. The revision dropdown for Modules is also now Maven coordinate backed, allowing for more consistent Module identification.
- Improvement - Apollo now displays Maven coordinate versions instead of Module revisions throughout all Module workflows. Additionally, some Module statistics such as installations, Products, and submodules are no longer shown directly in the Module list but remain available in the details panel when selecting a Module.
- Improvement - As of Apollo CLI version 0.463.0, the contact team flag for the
apollo-cli environment getcommand is optional. This changes ensures that Apollo CLI Environment commands work correctly for Environments without contact teams.
2025-07-15
Introducing dependency groups
Environment editors can now configure dependency groups to organize Entities into logical groupings. With dependency groups configured, an Entity will only consider a dependency satisfied if the dependency shares at least one group with the dependent Entity.
Dependency groups are useful when you want to run multiple instances of a Product in a single Environment. For example, you may want to run one instance of a Product for staging and another instance of the same Product for production. With dependency groups, different instances of the same Product can depend on different instances of another Product.
You can configure dependency groups by manually editing the Environment settings.
Learn more about dependency groups
2025-07-01
Other changes
- Improvement - A new Product column is now available in the Entity table on an Environment page. This column displays the Product associated with each Entity. The Product column is hidden by default, and users can change its visibility in the column settings. Hovering over a Product in this column displays additional information, and selecting a Product navigates to the Product page.
- Improvement - Users can now view Environment management settings even when they do not have edit permissions. Open the Manage Environment dialog to view the settings in read-only mode, with disabled fields and a message indicating the settings cannot be edited.
- Improvement - Apollo now displays the required Product Release labels constraint when defining a promotion pipeline. Users can view label requirements specified on a canary promotion for their Product, ensuring visibility of all constraints in the promotion workflow.
- Improvement - Team notifications now include a direct link to the change request search page with a pre-applied filter showing change requests pending approval from that team. This allows team members to quickly access and review all change requests awaiting their team's response.
- Improvement - Modules in Apollo now display their sharing status in the header and use Product-based RBAC and labels. The Module details panel has been improved with a more consistent loading experience, and the labels widget now properly reflects product information.
- Improvement - Apollo now enforces validation rules when deleting Modules and Module revisions. Shared Modules cannot be deleted, and Modules that have releases used as submodules in other Modules are protected from deletion. These validations are displayed in the user interface with appropriate action disabling and explanatory messages.
2025-06-23
Apollo CLI command deprecation
The following Apollo CLI commands have been Deprecated and will be deleted in December 2025:
- apollo-cli create-product-tgz helm-chart
- apollo-cli create-product-tgz manifest
- apollo-cli get-installations
- apollo-cli get-product-releases
- apollo-cli get-product-versions
- apollo-cli installation create asset
- apollo-cli list-products
- apollo-cli manifest create helm-chart
- apollo-cli manifest verify
- apollo-cli module submodule-update
- apollo-cli publish artifact
- apollo-cli publish asset
- apollo-cli publish helm-chart
- apollo-cli publish manifest
- apollo-cli publish terraform-module
2025-06-16
Introducing Apollo notifications
Apollo notifications enables you stay informed about changes to your Products, Environments, and teams. With Apollo notifications, you can:
- Configure notifications across multiple channels (email, Slack, or in-app)
- Set up both user and team notifications
- Customize notification preferences for specific resources
- Receive alerts for Product recalls, RBAC changes, promotion failures, and more
Apollo notifications are designed to help you keep track of important changes in your infrastructure. You can easily configure notifications for resources you own or subscribe to notifications for resources managed by other teams.
To learn more about setting up and managing notifications, review the documentation:
2025-06-05
Suppression windows and maintenance window overrides
This update introduces new visibility into suppression windows and maintenance window overrides.
You can now view suppression windows and maintenance window overrides for an Environment and its Entities by navigating to the Settings tab for the Environment and selecting Maintenance and Suppressions.
You can also view suppression windows and maintenance window overrides for an Environment or Entity by navigating to the Environment or Entity page and selecting Overrides and Suppressions from the Activity tab.
Review the documentation to learn more:
Cancel active Plans
Apollo now supports multiple ways to cancel active Plans for an Environment or Entity.
To cancel active Plans for an Environment or Entity, you can now select the Cancel active plan action from the Actions dropdown for the Environment or Entity.
To cancel specific active Plans for an Environment or Entity, you can navigate to an active Plan in the Activity tab and select Cancel active plan from the Actions dropdown.
Learn more about canceling active Plans for Environments and Entities.
2025-06-03
Other changes
- Improvement - The Module installation workflow now suggests variable values based on existing installations. When configuring a new Module installation, Apollo identifies Entities that are already managed by existing Module installations and presents variable value suggestions. If the new installation is configured to manage Entities that are already managed by existing Modules, users are prompted to unlink those existing installations before proceeding.
- Improvement - Apollo now displays "View change request" as a clickable link for change requests without titles. This ensures users can navigate to any change request from the table view, even when the change request has no title.
- Improvement - Apollo now provides a direct way to remove suppression windows and maintenance window overrides by adding an action in the suppression and maintenance window override banners. Users can select the new delete button that appears when hovering over items in the popover, which opens a confirmation dialog before removal.
- Improvement - The Module variable update dialog now provides validation feedback. When users attempt to update variables with values that would create conflicts, such as when an Entity is already managed by another installation, the dialog displays an error message and disables the submit button until the conflict is resolved.
- Improvement - The teams page of the Apollo Hub settings now features a dedicated Contacts tab. Users can create and manage team contact methods through this interface, replacing the previous Edit team details action. Each contact can be configured to receive notifications when notifications are enabled for a Hub. For example, if a Slack channel is specified as a contact method, notifications will be delivered directly to that channel.
- Improvement - Users can now cancel all active Plans for an Environment at once. This action is available in the Environment actions dropdown menu. When canceling Plans, users can include a rationale and choose whether to automatically create a suppression window after cancellation.
- Improvement - Apollo now provides a restart command for Deployment and StatefulSet resources in Helm charts. Users can access this action directly from the resources graph. When initiated, a banner appears in the resource details to track the restart operation's progress.
2025-05-20
Environment settings improvements
This update introduces improvements to the Environment Settings tab.
Artifact Registries
You can assign Artifact Registries to an Environment from the Environment's Settings tab. You can also view the Artifact Registries that have already been assigned to the Environment.
Maintenance and suppression windows
The maintenance and suppression windows for an Environment and its Entities are now displayed in the Environment settings. You can now create and update maintenance and suppression windows from the Environment Settings tab.
Display metadata
You can now provide the following for your Environment:
- Display name: A name for the Environment. The display name will replace the Environment name in Apollo.
- Description: A brief summary of the Environment.
- README: Essential information about the Environment. The README supports Markdown rendering.
2025-05-06
Environment Apollo CLI commands part of Standard Support Policy
The apollo-cli environment commands are now part of our Standard Support Policy and are no longer Experimental.
Apollo CLI command deprecation
The following Apollo CLI commands have been Deprecated and will be deleted in November 2025:
- apollo-cli add-unmanaged-service
- apollo-cli create-module
- apollo-cli list-environments
- apollo-cli list-namespaces
- apollo-cli create-environment
- apollo-cli delete-environment
- apollo-cli generate-agent-manifest
Other changes
- Improvement - Apollo's Entities tab now features a K8s Namespace field in the histogram, allowing users to filter Entities by Kubernetes namespace. The Kubernetes namespace filter can be included in the URL parameters to automatically select the filters on page load.
- Improvement - Apollo now intelligently manages the display of the Product description widget on the Releases tab. When no description is set, the widget is hidden for users without edit permissions, optimizing screen space. Users with edit permissions will see an empty widget with a prompt to add a description.
- Improvement - The Environment suppression banner now exclusively shows Environment-level suppressions, while the Entity-level suppression banner continues to display both Environment and Entity-level suppressions. This update enhances the visibility of suppression information.
- Improvement - Maintenance window override banners are now displayed on Environment and Entity pages. When a maintenance window is active, users can view a banner notification and select the right side popover for more details. If both suppression windows and maintenance windows are active simultaneously, the suppression window takes priority in the display, with maintenance window information available in a collapsed format.
- Improvement - When searching in your notifications inbox for items that do not exist, your currently selected item will now remain visible. A new visual guide now appears when you have no notifications, providing clearer direction.
- Improvement - The Environment suppressions table features a new type-based filtering feature. Users can refine their view by selecting from various suppression categories, including
Manual,Automatic - Failed Plan,Automatic - Failed Blue Green Upgrade, andAutomatic - Release Promotion. - Improvement - The target version selector for issuing commands now offers expanded metadata for Entity commands. Users can view recall status, recent blue-green upgrade green version information, and total Entity count across Environments. When selecting a version, intermediate Releases are listed with the same comprehensive metadata.
- Improvement - Apollo now provides a unified experience for deleting maintenance windows. When removing maintenance windows from blocking conditions, a confirmation dialog displays the number of windows to be deleted. Additionally, a tooltip now appears when all blocking maintenance windows have already ended, providing clearer status information across Environments and Entities.
- Improvement - Apollo now prevents deletion of Artifact Registries that are still reported in Environments, avoiding potential errors. The user interface has been enhanced to show all Environments where a registry is reported in the registry's assigned Environments list. Additionally, Environments now display registries that are reported but not assigned, with the option to add them back through change requests.
- Improvement - Users can now select a cloud account when installing Terraform modules. The field automatically populates with available accounts. If account information cannot be retrieved, a text input field is provided instead. This field is required to complete the installation process.
- Improvement - Apollo now displays short descriptions in the headers of Environment and Product pages. Users can add and edit these descriptions through the resource metadata settings. Additionally, a README field has been added to resource metadata settings, and the Product README field has been generalized to work with all resource types.
- Improvement - Entities now support a new action to cancel active Plans. Users can access this feature through the Entity actions menu, which opens a dialog to cancel any ongoing automatic operations. The dialog includes a rationale text box for documenting cancellation reasons and an option to automatically open a suppression window (enabled by default). A notification appears if no active Plans are found for the Entity.
- Improvement - The Module Contents tab now displays both a graph representation and the contents inbox in a single view. Users can resize these views by dragging the divider between them. This integrated approach replaces the previous separate Graph tab, allowing for easier visualization of Module composition while maintaining access to the contents list.
- Fix - Apollo now automatically refreshes Team information after changes, eliminating the need for manual page reloads. This enhancement ensures immediate visibility of updates to Slack channels, emails, and PagerDuty contacts in the Team details.
2025-04-01
Other changes
- Improvement - Users can now delete a specific release of a Module directly from the Module release page. This feature includes built-in safeguards, such as permission verification, installation status checks, and parent Module dependency validation, ensuring safe and controlled deletion processes.
- Improvement - Introduced enhanced functionality for managing maintenance windows directly from the settings page. Users can access a new edit action that redirects to the Environment configuration, with the maintenance window block pre-selected for immediate modifications. This update extends to both no-downtime and downtime maintenance items, allowing for quick navigation to specific sub-properties within the maintenance window section.
- Improvement - Apollo now displays maintenance window banners for Environments, showcasing all active suppression windows. This update improves clarity in high-traffic environments. Additionally, users can now select the Apollo Entity IDs to view the Entity page, facilitating easier navigation within the platform.
- Improvement - Apollo now displays error messages for disconnected Artifact Registries directly in a tooltip when hovering over the registry. This enhancement provides users with immediate feedback on connection issues, streamlining troubleshooting efforts.
- Improvement - Added validation to enforce timezone specification when defining maintenance windows in Product settings. This validation ensures that maintenance windows are properly configured, preventing submission errors and improving scheduling accuracy.
- Improvement - Introduced a revamped Teams view featuring an inbox component design. This update includes a dedicated Notifications tab and consolidates existing features into a comprehensive Overview tab. This new Overview tab incorporates Membership, Team Properties, Labels, and Roles widgets. Team selection now utilizes the inbox panel, replacing the previous dropdown in the header.
- Fix - We've optimized the blue/green event overflow list functionality for small screens, addressing several user interface improvements. The update eliminates excessive scrolling by collapsing items, removes the display of
0 more eventswhen no additional events exist, and ensures complete visibility of event titles.
2025-01-13
Module Apollo CLI commands part of Standard Support Policy
All Apollo CLI Module commands are now part of our Standard Support Policy and are no longer Experimental.
To begin using these commands, you can re-download the Apollo CLI.
2024-12-03
Composite Modules
Composite Modules allow you to create a Module from other existing Modules. This enables you to manage complex configurations by breaking them down into smaller, reusable components called "submodules".
With composite Modules, you can customize the variables of the Modules that you include as submodules. You can also customize the configurations and secrets of any entities defined in submodules.
Learn more about composite Modules.
2024-11-26
Introducing Artifact Registries
Apollo now supports directly integrating with your existing OCI registry to allow the management and deployment of software directly from your registry. Rather than publishing containers for Product Releases directly to Apollo's Container Registry, you can link your existing OCI registry to Apollo and create Product Releases in Apollo that reference artifacts from your own OCI Registry.
Learn more about Artifact Registries.
2024-07-08
Improvements to promotion pipelines
This update introduces improvements to how you can configure promotion pipelines.
Apollo now supports dynamic Environment strategies for promotion pipelines. With these strategies, Apollo evaluates conditions on a dynamic set of Environments, chosen with filters. To enable this, you can select Canary promotion when configuring a promotion stage.
Learn more about canary promotion stages.
2024-06-13
Risk management improvements
This update introduces several improvements to how you can view and manage vulnerabilities.
Apollo now differentiates between vulnerabilities, which may impact many resources, and findings, which are surfaced through scans and identify the specific resource where a vulnerability was found. Each table in the Risk Management applications will only surface a vulnerability once.
Risk Management application
The Risk Management application enables you view all the active vulnerabilities detected in Product Releases on your Apollo Hub. You can select vulnerabilities to view information such as risk scores, paths to files that contain the vulnerability, fix versions, and affected Entities.
In addition to the global context, the Risk Management application is also available in the context of a specific Environment through the Environment Security tab.
You can also use the Risk Management application to create suppressions for vulnerabilities.
Suppression scopes
When suppressing a vulnerability that has multiple findings, you can now set a suppression scope that defines what findings Apollo will suppress. You can suppress findings on a specific image, image prefix, or for the distribution bundle of a Product. You can also suppress the finding across all deployed Products.
Additionally, we have made updates to core workflows of requesting a suppression, identifying other affected resources, and re-running vulnerability scans after creating a suppression.
2024-06-11
Improvements to secret creation
This update introduces several improvements to how you can manage secrets in Apollo.
You can now create secrets for an Entity at installation time. To do this, use the new Add secrets option in the Entity installation form. Apollo will create the secret in the Environment when it installs the Entity.
When editing secrets, you can now view existing secret keys. In addition, you can now change some key-value pairs in a secret without modifying others.
Learn more about creating and editing secrets in Apollo.
2024-05-31
Other changes
- Improvement - Users can now submit empty values for Module variables.
- Improvement - Added a link to the Teams page in the Apollo home page.
- Improvement - Improved error messages for failed manifest downloads that are caused by a missing root operator.
- Improvement - Added the Agent ID and a link to the Entity in the Metadata section for unsuccessful Plans.
- Improvement - Apollo now supports deleting Products that have over 1000 Releases.
- Improvement - Users will no longer close the install Entity dialog when they click outside of it.
- Improvement - Added Entity name validation to the install Entity dialog. Apollo will now verify that an Entity starts and ends with an alphanumeric character and only contains alphanumeric characters,
-,_, and.. - Fix - Fixed an issue where large numbers in the Entities column of the Releases table were ellipsized.
2024-05-16
apollo-cli get-central-namespace command is Deprecated
The apollo-cli get-central-namespace command is now Deprecated. It will be deleted in November 2024.
2024-05-02
Automatic approvals for Module updates
After you edit a Module and Apollo generates a change request to update every installation of the Module, Apollo can now automatically approve the change request.
You can enable automatic approvals for Module updates like marking Entities for uninstallation, changing the default Release Channel, adding a new Entity, and more.
Learn more about automatic approvals.
2024-04-30
Other changes
- Improvement - Added a progress bar to the Export page to display the progress for bundles. Apollo will display a blue, striped bar for an in-progress bundle and a red bar for a failed stage.
- Improvement - Apollo can now automatically resolve merge conflicts on change requests for Module installations or updates. To do this, users can select Automatically resolve merge conflicts on a change request for a Module installation or update that has a merge conflict.
- Improvement - The Product creation workflow now validates inputs for group ID and artifact ID.
- Fix - Fixed an issue where the promotion pipeline form failed to validate when Require test environments was disabled.
2024-03-29
Other changes
- Improvement - Improved the Product creation workflow by separating the Product details form and the generated code into separate steps.
- Improvement - Added an Entities column to the Module Installations table. Hover over the status bar to view the number of Entities in the Module and their upgrade status.
- Improvement - Added status tags to the Environment and Version columns of the Module Installations table. Hover over these tags to view more information on the version of the Module installed in the Environment and if there is a newer version of the Module that can be installed.
- Improvement - Added a details panel to the Entities table of the Environment page. Select an Entity from the table to view information such as the version, Release Channel, Entity health, applied labels, and more.
- Fix - Fixed the width of the Recalls tab on the Product page.
2024-03-19
Improvements to Modules workflows
This update introduces several improvements to how you update and manage Module installations in your Environments.
Update Module installations
After you edit a Module, Apollo will now automatically attempt to update all installations of the Module. You can view the available updates for each installation of the Module in the Installations tab of the Module overview page.
You can also update a Module installation manually by following same steps as when installing a Module.
Learn more about updating Module installations.
Mark Entities for uninstallation
You can now mark Entities for uninstallation in the Module YAML file:
Copied!1 2 3markedForUninstallation: minVersion: 1.0.0 unmanageAfterUninstall: AUTOMATIC
Marking the Entity for uninstallation in the Module definition will ensure that the Entity is uninstalled from the Environment when the Module is updated. If you simply remove the Entity from the Module definition, the Entity will not be uninstalled from the Environment when the Module is updated.
Unlink Modules
You can now unlink a Module from an Environment to remove the Module installation. The Entities that were part of the Module will remain in the Environment after the Module is unlinked but will no longer be managed by the Module.
Learn more about unlinking Modules.
2024-03-14
Product Release incompatibilities
Apollo now supports Product Release incompatibilities. This allows you to declare that a Product Release is incompatible with a range of other Product Releases. Apollo will ensure that Product Releases that are incompatible with each other are not installed in the same Environment at the same time.
You can define Product Release incompatibilities in the Product Release manifest:
Copied!1 2 3 4 5 6 7extensions: product-incompatibilities: - product-group: org.postgresql product-name: postgresql product-type: helm-chart minimum-version: 9.3.6 maximum-version: 9.6.x
Learn more about configuring Product Release incompatibilities.
2024-03-12
Experimental Apollo CLI commands
This update introduces Experimental commands for the following Apollo resources:
View an example end-to-end workflow using the new commands.
To begin using these commands, you can re-download the Apollo CLI.
2024-02-29
Other Changes
- Improvement - When uninstalling Entities, users can now optionally enter a title and rationale for the change request that will be created.
- Improvement - A warning banner will now appear on an Entity page if the Entity is stuck in
Install pendingstate. - Fix - Apollo will now display the full label name for labels with URL values.
- Fix - Fixed an issue where default values for a Module did not appear in the Contents tab.
- Fix - Fixed an issue where the final step of the Product publishing form would become unresponsive.
2024-01-31
Improved Entity uninstallation
This update introduces several improvements to how you uninstall Entities from an Environment in Apollo.
After you uninstall a local Entity, Apollo will unmanage the Entity by removing it from the Environment settings.
For remote Entities, you can uninstall the Entity from the source Hub and then transfer the update in a bundle to the target Hub. After the Entity is uninstalled from the target Hub and you confirm this from the source Hub, Apollo will unmanage the Entity by removing it from the Environment settings.
Learn more about uninstalling local and remote Entities.
Other Changes
- Improvement - Added the Installations tab to the Module page that displays the version, owner, and date last updated for each installation of the Module in an Environment.
- Fix - Fixed an issue where the end date for maintenance window overrides did not update properly.
- Fix - Fixed an issue where the Product publishing workflow did not generate the correct command for publishing Helm charts from OCI repositories to Apollo.
2023-12-14
Other Changes
- Improvement - Added a troubleshooting dialog for failed Plans. Navigate to a failed Plan from the Activity tab and select Troubleshoot failed plan to view the troubleshooting guide.
- Improvement - Added a banner to the Environment page when there is an active Environment-wide suppression window.
- Improvement - Bundle advisories are now displayed while a bundle is building.
- Fix - Fixed an issue where the Bundler showed an error state for empty namespaces.
- Fix - Removed the View failure button from successful and evaluating promotions.
2023-11-15
Other Changes
- Improvement - Users can view the history for a promotion without Test Environments by selecting the transition node for a promotion stage.
- Improvement - Added the Environment Overview tab for remote Environments.
- Improvement - Users can now specify a timezone for the expiry date when freezing all version changes as part of a recall.
- Improvement - Users can now add labels to an Entity by selecting Add labels from the Label history table of the Activity tab.
2023-10-15
Improved recalls
This update introduces several improvements to how you recall Releases in Apollo. To prevent shipping known bugs, users can now issue an open ended recall, and Apollo will auto-recall any new Releases. Users can edit the range of recalled Releases anytime to update the range of recalled Releases.
Users can also recall the same Release for different reasons. Apollo will intelligently resolve multiple recalls for a Release and ensure that Entities are rolled off bad Releases.
Learn more about improved recalls in Apollo.
Other Changes
- Improvement - Changes to a Product's settings will now be shown in the Changes tab of the Product home page.
- Fix - Removed the co-owner field from the Product details panel.
2023-09-15
Environment Overview tab
The first time you navigate to an Environment will land you on the new Environment Overview tab. This tab displays relevant information about an Environment, such as the owner, the default Release Channel, the labels applied to the Environment, and the maintenance windows. You can also view the upgrade status of Entities in the Environment and the status of Apollo Agents deployed in the Environment.
Other Changes
- Improvement - Users can now apply labels to Teams.
- Improvement - Users can now manage permissions for Environments and Entities using role-based access controls (RBAC).
2023-08-15
Activity tab
The Activity tab for Entities and Environments allows you to view Plans, commands, and upgrades in a single tab. This tab displays any blocking constraints for ongoing work, as well as the status of completed work.
Other Changes
- Improvement - Users can now be added directly to Apollo Teams.
2023-07-15
Other Changes
- Improvement - Users can now filter change requests by author.
- Improvement - View Plans to upgrade Entities to new Releases and any constraints blocking them in the Upgrades tab of the Entity home page.
2023-06-15
Labels for Entities and Environments
This update introduces labels for Entities and Environments. Add labels to these resources to tag with them information that is key to your organization or software operations. Then, use labels to filter the list of Entities or Environments based on specific properties.
Other Changes
- Improvement - Added support for deleting Products and Product Releases in Apollo.
2023-05-15
Promote up to chosen channel
This feature provides a single workflow entry point to manually add a Release to a Release Channel. With this manual promotion workflow, the break-glass operation of adding a Release to a Release Channel scales to match the ability to configure complex promotion pipelines.
Other Changes
- Improvement - Added support for AgentIds to be arbitrary strings.
- Improvement - Added date range filters to the Change Request page. Users can filter by the date and time that a change request was created or last updated.
2023-04-30
Other Changes
- Improvement - Users can now reference user-defined secrets in Helm chart config overrides. Secret changes will appear as a Plan for an Entity.
- Improvement - Added a filter to Release table on a Product overview page. Users can filter the list of Releases by Release Channel or recall status.
- Fix - The Upgrade tab of the Entity overview page now specifies the required maintenance window, either downtime or no-downtime, when an upgrade is blocked.
2023-03-31
Other Changes
- Improvement - Added status and rollout bars that display the number of Entities that are up to date, currently upgrading, in grace period, and blocked.
2023-02-28
Other Changes
- Improvement - Improved functionality of the suppressions table, adding indicator for out of date suppressions, filtering, sorting, and bulk actions.
- Improvement - Added the Changes tab on the Product overview page where users can view change requests for that Product.
- Improvement - Users can now add and edit labels on a Release by selecting Edit labels from the Actions dropdown.
- Improvement - Improved the messages displayed when a Release is recalled.
- Improvement - Improved the way promotion constraint results, such as Product maintenance windows and health status checks, are surfaced to users.
- Improvement - Added filters to the Environments table. Users can now filter the list of Environments by owner, accreditation, namespace, or label.
2023-01-31
Environment Config
This update adds support for managed Environment Configs to Apollo.
Common configuration values, such as domain names, may be useful across many Entities in an Environment. Prior to this update, these shared values had to be provided to Entities through bespoke systems in your Environment, or stored many times in each Entity Config in Apollo. Either solution meant more work for Environment owners and less clear visibility into shared values.
Apollo now supports managed Environment Config through a similar workflow as available for each Entity. These values are also represented in each Entity Config tab to make sure every operator in the Environment knows about them and Pans for each Entity include both Config values. Changes to these values go through standard Change Management processes, and updates are propagated to each Entity through rolling Plans across the Environment.
Improved Release Promotion Graph
Promotion Stages between Release Channels support flexible rollout strategies across environments for your products. To make it easier to manage these promotion stages, the Release "Canary Analysis" tab has been replaced with comprehensive "Promotion" workflows.
The Promotion Graph clarifies the representation of complex branching pipelines in the Apollo interface and makes it easier to interpret the observations that led to automated action. Interactive components now provide in-context answers to key questions about automated recall, pending upgrades, in-flight promotion constraints, and more.
Other Changes
- Improvement - Moved the product "History" tab to the main "Details" view to simplify navigation.
- Improvement - Added tooltips explaining how suppressions applied to environments impact plan recommendation.
- Improvement - Added a new graphic to the Bundler landing page to explain bundling workflows to new users.
- Improvement - Added a default namespace feature that automatically lands the user on their last viewed namespace upon navigating to the bundler.
- Improvement - Improved Change Request rejection messages for users when one or more requirements are disapproved.
- Improvement - Enabled sharable links for bundles.
- Improvement - Improved styling and legibility for warnings encountered during remote bundling workflows.
- Improvement - Improved warnings for users when the reported state from an environment for an entity is out of date.
- Improvement - Cleaned up indentation on bundle contents page and sorted contents by version.
- Improvement - Dynamically rendered the bundler menu popover depending on a user’s access to the bundler, unbundler, or both.
- Fix - Added pagination to view bundles past the most recent fifty that had been built.
2022-12-16
New Admin Permissions Panel
There is now a Permissions panel in Settings that provides visibility into the roles that exist for each context and who they are granted to. Previously, root role grants for various resource types in Apollo were inaccessible to end-users, requiring Palantir intervention to set appropriate admin teams or groups for each context. Now, root admins can use the Permissions panel to independently set access for roles.
Other Changes
- Improvement - Added sort and search capabilities to the list of products bundled to a remote namespace.
- Improvement - Improved styling for common inbox components reused through the application.
- Fix - Addressed performance problems with rationale inputs in break-glass commands.
- Fix - Fixed various data consistency or status representation problems in bundler workflow.
2022-11-30
Other Changes
- Improvement - Add a list of team members to popover details provided in context of change requests or other entity ownership.
- Improvement - Add an impact preview to change requests for Environment config.
- Improvement - Added support for releases in the catalog that will not yet be recommended for installation due to missing container images.
- Improvement - Better represented Apollo Agents and their last check-in time during the environment bootstrap sequence.
- Improvement - Added initial support for modern product release labels, attribution, and label history.
- Fix - Improved error messaging for Environments with the Apollo Control Plane improperly configured.
- Fix - Prevent the application from crashing when expanding details for a plan that impacts multiple entities.
2022-10-31
Environment Templates
Environments managed by Apollo must include a well-defined set of control plane services; the "Create Environment" workflow now contains a set of predefined options for your control plane. These options help operators make an informed decision about which services are relevant to a use case and prevent problems with misconfigured environments.
Other Changes
- Deprecation - Migrated and removed legacy release labels to prepare for modern user-driven release labels.
- Improvement - Added a dialog walking through the release registration process to support "New Product" workflows.
- Improvement - Represented statuses more clearly in all managed entity lists.
- Improvement - Added teams for which you are a member to the top of team select lists and more clearly represented your membership.
- Improvement - Added more detailed failure messages for plans.
- Improvement - Added clearer error messages for Change Requests that are improperly formatted.
- Improvement - Addressed several key latency or performance problems in the Bundler application.
- Improvement - Added a troubleshooting guide to help with common problems during the environment bootstrap sequence.
- Improvement - Added an action to cancel a bundle build job.
- Improvement - Changed the control plane to leverage a default storage class unless an override is provided.
- Improvement - Added a landing page for the Bundler application.
- Improvement - Improved sidebar navigation for the Bundler and Unbundler applications.
- Improvement - Added more robust multi-select interactions for resource tables to support bulk operations.
- Improvement - Improved user experience, validation and error messages in release promotion pipeline setup workflows.
- Fix - Changed the color of the "Deferring" health check status to better differentiate it from other statuses.
- Fix - Prevented health check popovers from growing too tall to be fully visible where many parameters are provided.
- Fix - Improved "Add Helm Chart" form field edge case validation, smart defaults, and user-facing messages.
2022-09-30
Other Changes
- Improvement - Improved Helm charts support in Apollo to address spurious install plans and unexpected or opaque plan failures.
- Improvement - Improved the components used for "Advanced Filters" in list views.
- Improvement - Improved access to basic details and actions directly within the Environments list.
- Improvement - Added better errors during K8s Environment manifest generation.
- Improvement - Added a filter to the products list for a user's owned products.
- Improvement - Added a component to Release recall callouts to better surface recall history.
- Improvement - Supported requiring approval for suppression windows.
- Improvement - Improved the product registration dialog with clear Apollo CLI access and pre-populated commands.
- Improvement - Added Product settings to the Product details panel to improve visibility into key properties.
- Improvement - Surfaced optionally dependent Entities during delete workflows more clearly.
- Improvement - Added an action to the Environment actions dropdown to access the Environment Setup Guide.
- Improvement - Added the ability to filter product releases based on Release Channel inclusion.
- Improvement - Added an action to edit Product settings to the actions dropdown in single Product views.
- Improvement - Added a filter to the Environments list to only owned Environments.
- Improvement - Changed multiple components to surface namespace concepts to users only when relevant.
- Fix - Fixed the count of remote namespace installations in product rollout workflow views.
- Fix - Fixed the count of installations tracking a release channel when manually promoting a release.
- Fix - Fixed duplicate horizontal scrollbars on the installation list views.
2022-08-30
Scanning for Vulnerabilities
Vulnerability scanning is critical for modern software security: given the number of open source components most software products use, discovered vulnerabilities will affect most product releases eventually. We are deeply integrating security scanning and scan result visibility into Apollo to help.
Product releases now have a "Security" tab that provides in-context access to results. Severe vulnerabilities will be subject to automatic release recall. This information is made visible for all operators to help them pinpoint in exactly which Products and Environments active vulnerabilities are deployed.
Environment Setup Guide
To make it easier for first-time Apollo users to manage an environment, we have introduced a dedicated in-app walkthrough to guide new environment owners through the steps required to connect an Apollo agent. This update also includes new manifest generation capabilities and a clear workflow to enable self-service setup for new users.
Other Changes
- Improvement - Updated Products views to show the Releases tab by default.
- Improvement - Supported deleting and restoring multiple Entities at once within an Environment.
- Improvement - Improved "restore" workflows for managed Entities after deletion.
- Improvement - Added support for break-glass commands for Helm Charts.
- Improvement - Added automatic refresh for plans lists so that users don't need to re-load the page manually.
- Improvement - Added environment namespace filters to the main Environment list.
- Improvement - Improved the styling and clarity for links to all entity types.
- Improvement - Improved the displayed statuses for break-glass commands executed by users in Apollo.
- Improvement - Provided a quick-copy button for key identifiers for Apollo concepts in details panels.
- Improvement - Added the "Override Maintenance Window" action to the individual Entity actions dropdown.
- Fix - Added more validations to Environment names during create workflows.
- Fix - Ensured capitalization is consistent for Release Channel names across the application.
- Fix - Ensured Change Request pop-up windows always link directly to the change request.
2022-07-29
Settings Approvals
Creating new environments or products along with many other settings updates were only possible for users with highly privileged administrative control within an Apollo organization. These changes are now all possible through the Change Request system. Any user can propose changes to settings, and the policy engine controls determine whether those actions are auto-approved or require a specific approval.
Other Changes
- Improvement - Switched the bottom drawer in the entity list to closed by default.
- Improvement - Updated the icons for core concepts in all usages across the application.
- Improvement - Ensured consistent styling for team, environment, and product lists.
- Improvement - Improved Install Map styles and colors.
- Improvement - Added the "created at" timestamp column to the product releases list.
- Improvement - Improved bundle list metadata to include size, creator, and status.
- Improvement - Combined multiple columns in the entity list to better leverage horizontal space on small screens.
- Improvement - Improved plan recommendation ordering for initial installation of complex platforms.
- Fix - Removed errant "Out of Date" warnings on several entity config views.
- Fix - Fixed a problem with browser forward or back navigation related to the deployment list search input.
- Fix - Ensured drawer selections are cleared in the Install Map any time the filtered scope changes.
- Fix - Improved the layout and overlap behavior of the Install Map on small screens.
- Fix - Removed all usages of "Deployment" terminology, preferring "Environment".
2022-07-01
Product Settings & Navigation
Ownership, promotion, and rollout settings for products can now be configured directly from the products list. These changes previously required navigating to a separate settings page. That page has been removed now that there is a clearer entrypoint.
Other Changes
- Improvement - Added rows for environments "pending creation" in the main navigation list after change request approval.
- Improvement - Removed the left entity sidebar in favor of a smaller right details panel.
- Improvement - Simplified the new entity dialog by moving some settings into an "advanced" section.
- Improvement - Introduced a simpler version-only input for initial entity config overrides.
- Fix - Switched to a bulk endpoint for entity health data to improve user-perceived latency.
2022-06-17
Apollo Home Page
We've added a new default landing page to Apollo, focused on providing more information about key Apollo concepts. In particular, this landing page describes Environments, products, and teams - concepts that Apollo users must understand and configure when getting started with the platform.
Apollo Public Documentation
You're reading this on the new public Apollo documentation site! Apollo's documentation will provide descriptions of core concepts, tutorials, and developer-focused specifications, and will be connected to the Apollo platform to provide specific help or context where appropriate.
Other Changes
- Improvement - Added a dropdown for supported versions of products to deploy during entity creation.
- Improvement - Moved some non-required fields to an "Advanced" form section in entity creation.
- Improvement - Added a "details" panel to install page.
- Improvement - Added Helm chart details to product release view.
- Improvement - Added a "details" panel to product release route.
- Improvement - Moved product settings into the primary product navigation list rather than the settings panels.
- Improvement - Introduced config actions to the environment's Actions button as a dialog.
- Fix - Added environment downtime approval constraints for break-glass commands with impact on quorum.
- Fix - Improved end-user perceived latency in the installation health inboxes.
- Fix - Fixed environments list scroll layout, sort alphabetically.
2022-06-10
The Payload Bundler
Many Apollo-supported installations of software are only accessible from specific air-gapped secure networks with strict data controls. That means that new releases of Apollo products need to go through a special process in order to be deployed into these environments.
Apollo supports this process through an application now available in the primary sidebar navigation called the Payload Bundler. Namespace owners are the primary users of the Payload Bundler: software operators who use Apollo to make sure the environments in these secure spaces are healthy and up-to-date. They can easily prepare and manage "bundles" of software with prepared updates for all tracked environments in a remote namespace. Apollo ensures these bundles contain the releases, settings, and metadata that are critical to keeping these critical applications and environments working.
Other Changes
- Improvement - Added the Namespace Details Panel to the Namespace Settings list to provide quick read-only access to key namespace properties.
- Improvement - Added the "Create Environment" button to the main environment list, in addition to the "Settings" environment list.
- Improvement - Made all environment settings actions available through menu options within the "Actions" button for an environment.
- Improvement - Moved environment suppression and maintenance window override controls into menu options within the "Actions" button for an environment.
- Improvement - Added an environment and namespace filter control to the main environment list.
- Improvement - Added options for "Additional requirements" for Change Request reviewers to power more complex compliance policies.
- Fix - Removed a duplicate scrollbar on the environment list and sort alphabetically by default.
2022-05-27
Team Membership Clarity
Authorization in Apollo is based on the concept of Teams. To make it easier to determine the team responsible for Products, Environments, or Installations, we have improved the interface for viewing a user's identity and team membership. The user settings page now includes a Profile & Preferences panel where you can see all teams for which the current user is a member or administrator. Additionally, the navigation sidebar now provides quick access to the full logged-in user ID, a logout button, and a link to the Profile & Preferences settings panel.
Other Changes
- Improvement - Improved Helm Chart upgrade and rollback behavior, especially for failure cases due to container availability problems.
- Improvement - Added a count to indicate the number of pending changes on the changes tab for environment and entity views.
- Improvement - Added a "session expired" dialog to guide the user to log in again when their login token expires.
- Improvement - Added a column to represent the number of entities on an environment from within the primary navigation list.
- Improvement - Added an option to group environments by namespace in the primary environment list.
- Improvement - Added the Product Details Panel to Product Settings list and Product Page views to show the product group, ownership, on-call, and key stats about the product.
- Improvement - Added a user profile popover to the main navigation sidebar. This popover provides one-click access to log-out of Apollo.
- Improvement - Added the Team Details Panel to Team Settings list and Team Page views. This panel clearly displays both group and individual roles for the team.
- Fix - Distinguished upgrade plans from config changes for pending plans in the upgrade tab of single entity views.
- Fix - Ensured the icons in the main navigation sidebar match the intended design.
- Fix - Provided better messages to users when missing entity health.
- Fix - Ensured the primary navigation search is available across all views.
2022-05-13
Modernized Sidebar Navigation
We've introduced an improved sidebar navigation component. This component contains quick links to all of the key concepts, owned environments, key tools or settings, and more.
Other Changes
- Improvement - Moved the filters in the Change Request inbox from top to left to better handle a large number of filter options.
- Improvement - Added an indicator for overall entity health status through a colored icon on the health tab.
- Improvement - Simplified and standardized resource headers within the application.
- Improvement - Cleaned up many polish or usability issues with the primary navigation sidebar.
- Fix - Improved long loading times on installation-specific change request views.
- Fix - Stopped using color on entire rows in installation tables to better draw attention to more actionanable status indicators in the row.