Vulnerability scanning
This page outlines how you can review vulnerability scan results and manually run vulnerability scans for Product Releases.
Viewing vulnerabilities
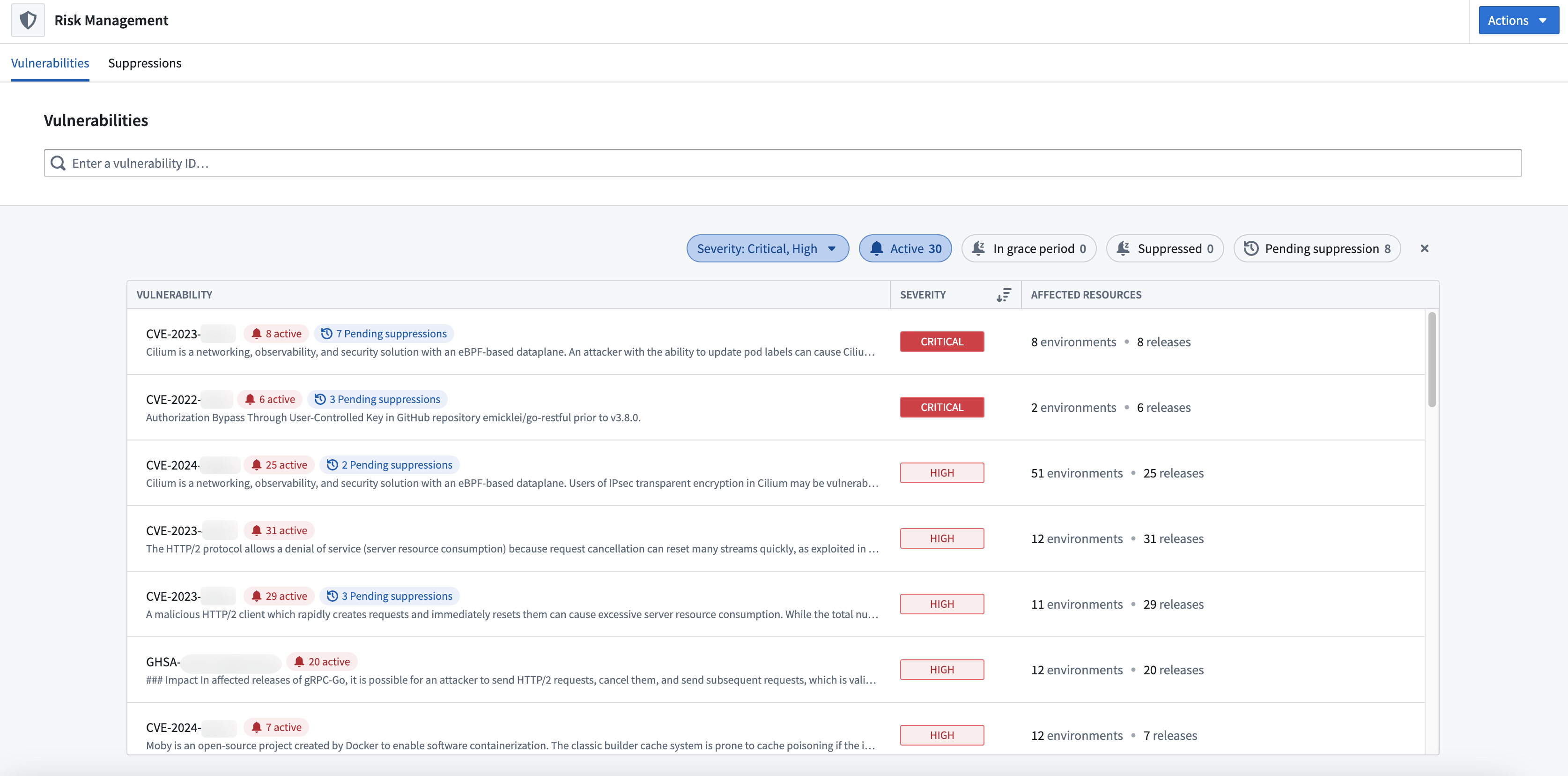
You can view the vulnerabilities for all Product Releases in your Apollo Hub in the Risk Management application. Select Risk Management from the Applications menu in the left sidebar.
The Vulnerabilities tab displays all the vulnerabilities found in all Product Releases.
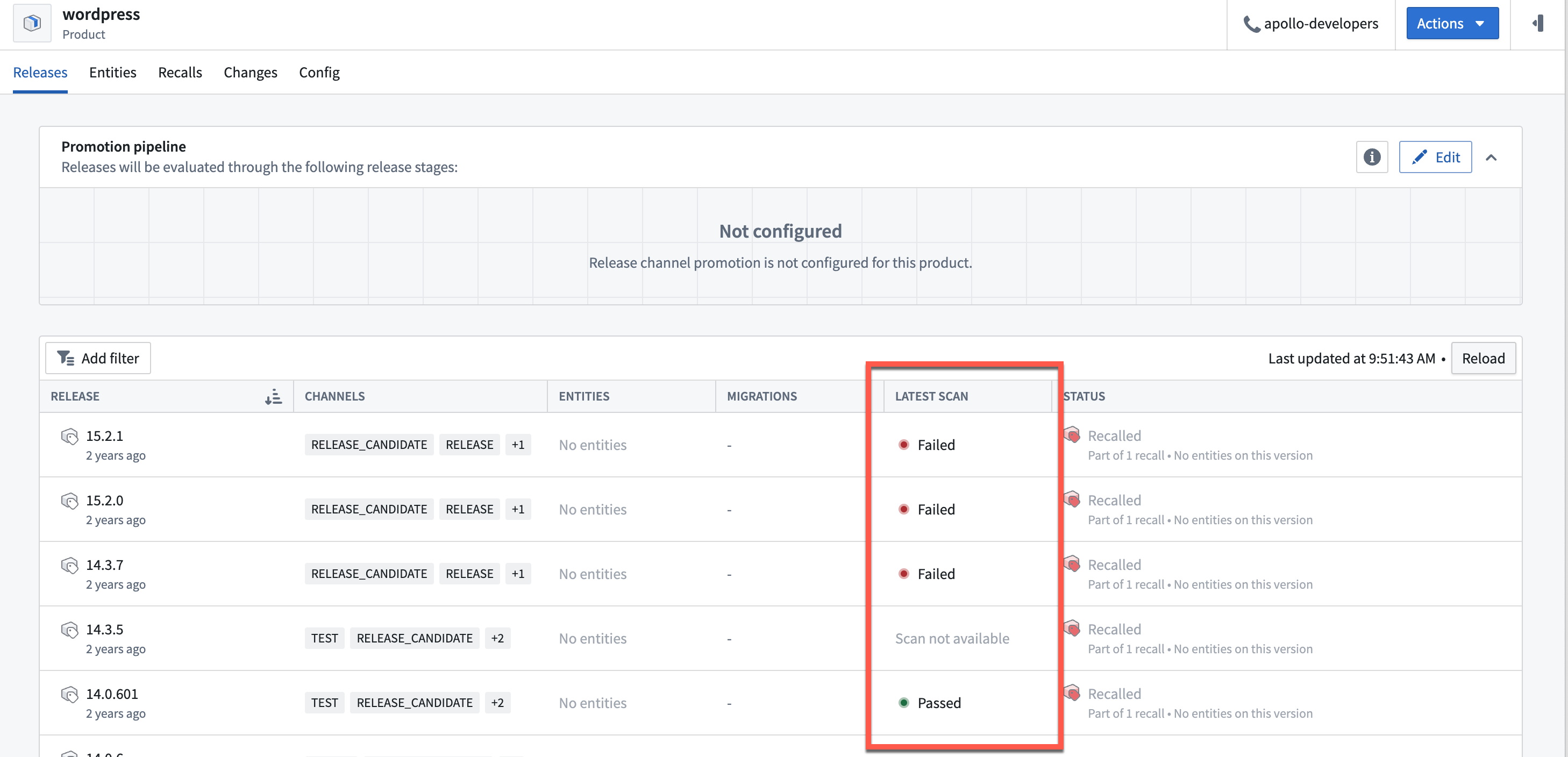
For a high level overview of vulnerabilities detected in Releases of a Product, you can navigate to the Product page and view the Latest Scan column in the Releases tab. There are three possible states for Releases:
Scan not available: A vulnerability scan has not yet happened for this Product Release.Passed: Apollo has scanned this Release and did not detected any vulnerabilities.Failed: Apollo has detected vulnerabilities in this Release that need to be actioned.
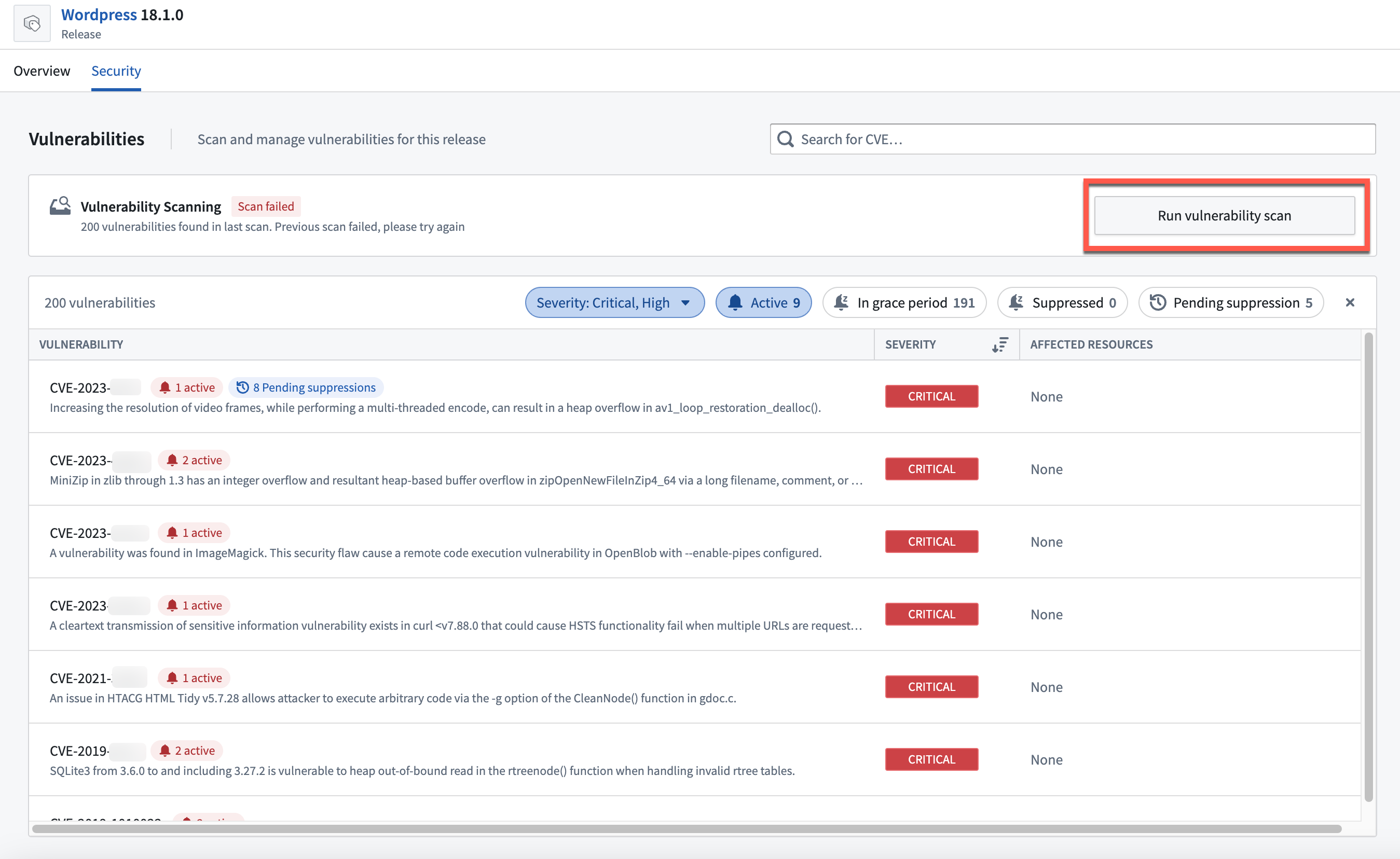
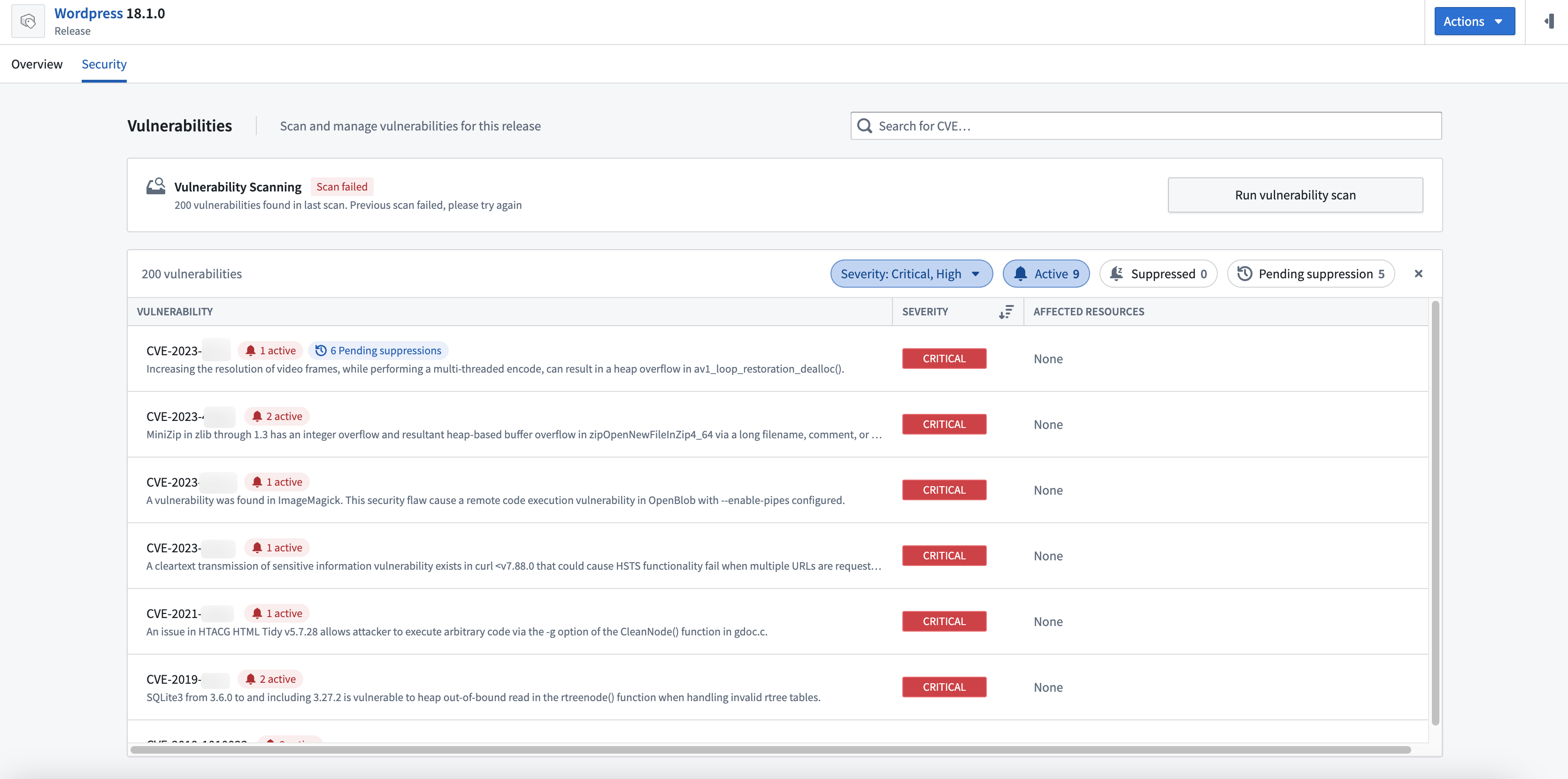
You can also find an overview of the vulnerabilities for a specific Product Release in the Security tab of the Release page.
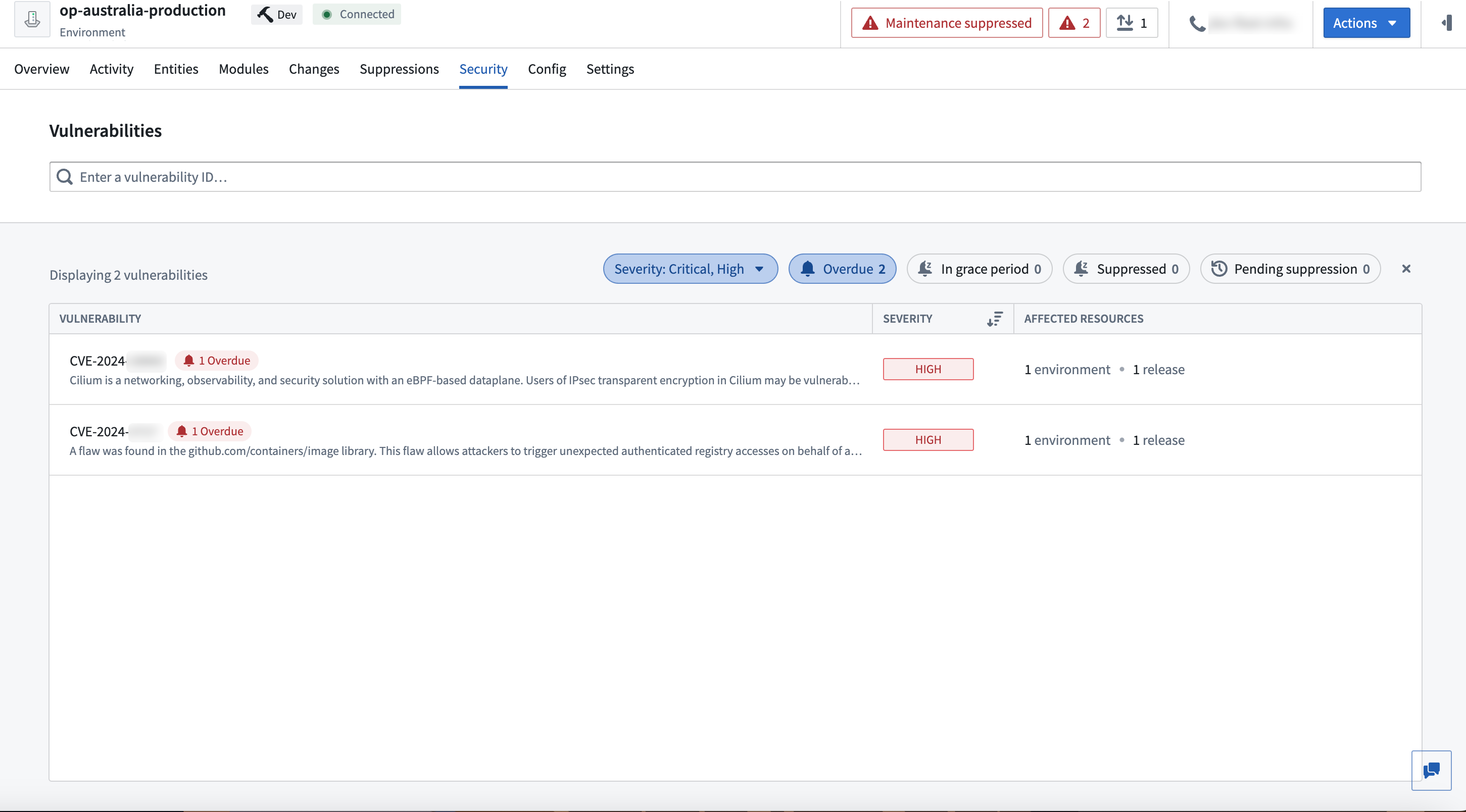
You can view an overview of the vulnerabilities for a specific Environment in the Security tab of the Environment page.
From any of these views, select a vulnerability to view more information.
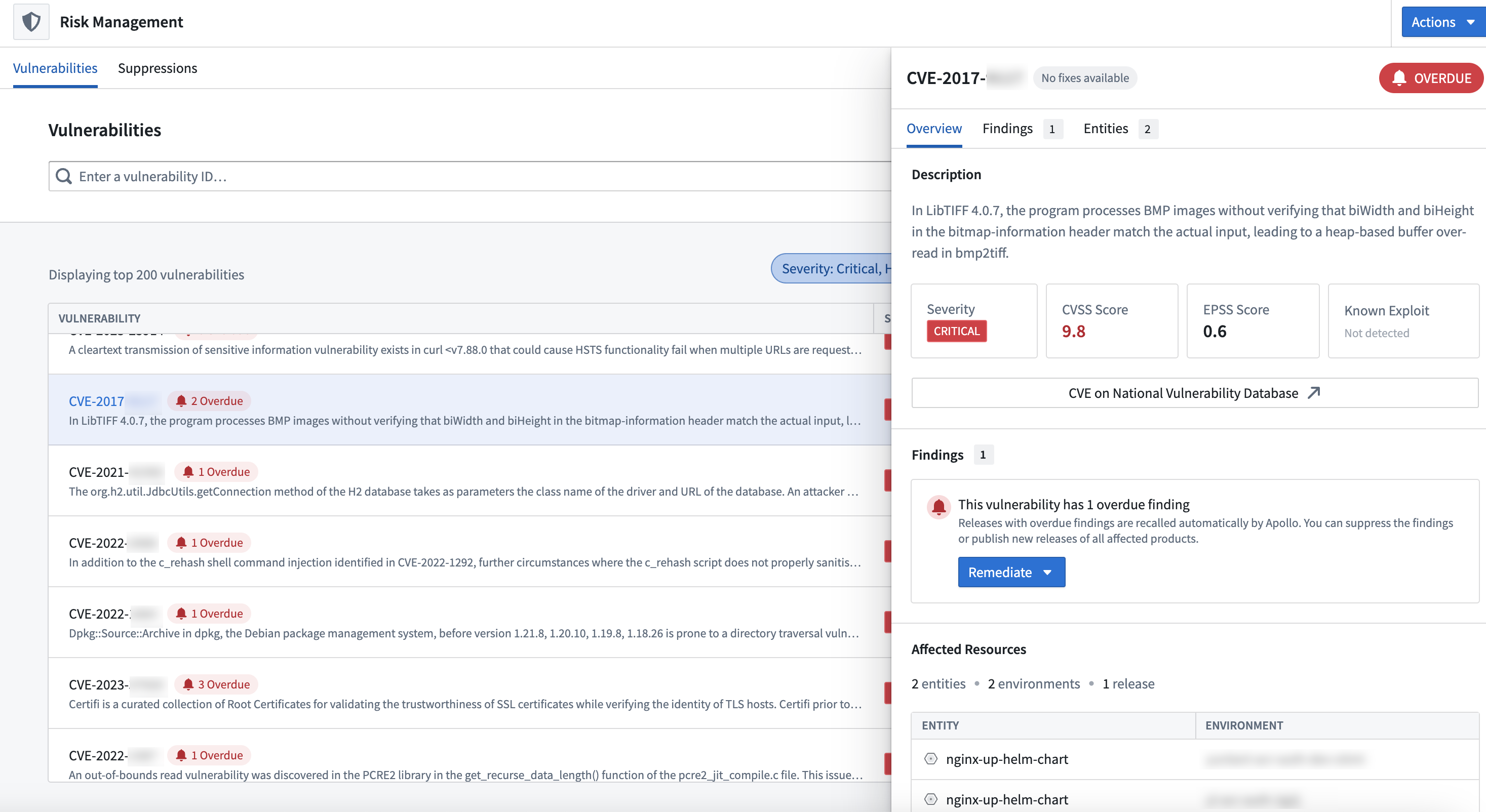
In the Overview tab you can view the risk scores.
Findings
Scanners run on regular cadence and identify specific vulnerabilities that are present in artifacts that are part of your Releases. This is determined by checking the artifacts which are defined as part of the Product Release manifest. These instances of vulnerabilities in a specific context are called findings. Apollo provides aggregate access to findings across a Product, Environment, or your entire managed fleet of software Entities. Suppression workflows mute one or more findings at a time, based on the characteristic of the finding that will be surfaced in successive scans.
Navigate to the Findings tab to view the Release(s) in which the vulnerability has been found. You can select a Release to view the affected packages, the vulnerable versions, and a fix version if one is available.
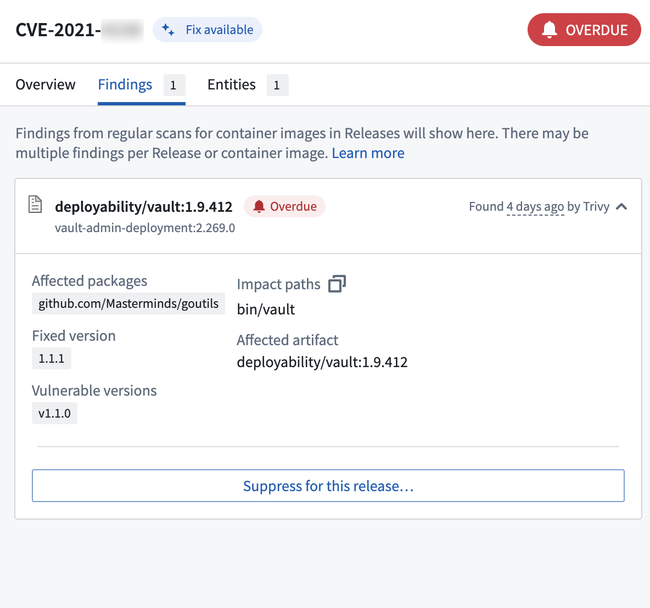
Affected resources
Select the Entities tab to view the Entities that have the vulnerable Product Releases installed.
Generally, Product editors should use this information to determine how to resolve the CVE in their Product by creating a new Release that addresses the vulnerability. If you are installing a third-party product, then you can create a new Release when a fix becomes available.
Resolve image scan failures
To remediate an image scan failure, you can upgrade your image or remove the vulnerable components to avoid these CVEs and create a new Release.
If these CVEs are a false positive or if you cannot remove them and have introduced mitigating controls instead, you can request a vulnerability suppression.
Release artifacts are considered immutable by Apollo. To resolve a vulnerability, you should create a new Release of the Product rather than re-scanning a Release, or you should suppress the vulnerability and then re-scan the Release. The next scan will reflect the status of suppressed findings.
Automatic recalls based on vulnerabilities
By default, all Product Releases with active vulnerabilities will be automatically recalled if there are no human requested or grace period suppressions. If you want to disable this, contact your Palantir representative.
Automatic recalls based on vulnerabilities use a roll-forward selection strategy.
Manually run vulnerability scans
In cases where you cannot wait for the next vulnerability scan for a suppression to be applied, you can manually run a vulnerability scan for a Release.
You can run a vulnerability scan by navigating to the Security tab of the Product Release page and selecting Run vulnerability scan.