Configure the AWS ECR secret connector [Experimental]
This is an Experimental feature that may not be available on your Apollo Hub. Contact your Palantir representative to learn more.
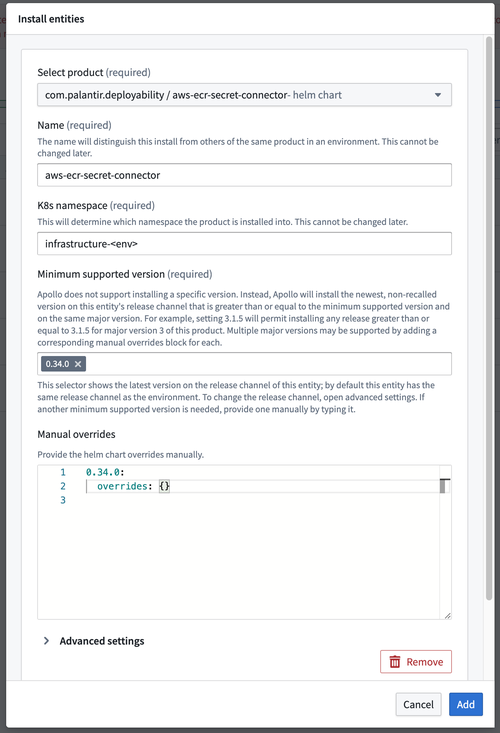
This guide will walk through how to install the Amazon Web Services (AWS) Elastic Container Registry (ECR) secret connector in your Environment.
-
Install the
aws-ecr-secret-connectorProduct in your Environment.-
Enter the
infrastructure-<env>namespace in the K8s namespace field. -
Leave the Manual overrides section set to the default.
-
-
Create a secret in Apollo for the newly installed
aws-ecr-secret-connectorEntity, for example,<secret-name>.
-
Take note of the secret name.
-
You should add the following keys:
accesskeyidandsecretaccesskey. The values should be the credentials for your AWS IAM principal. Note: these keys are different than the conventionalAWS_ACCESS_KEY_IDandAWS_SECRET_ACCESS_KEYused for the AWS CLI.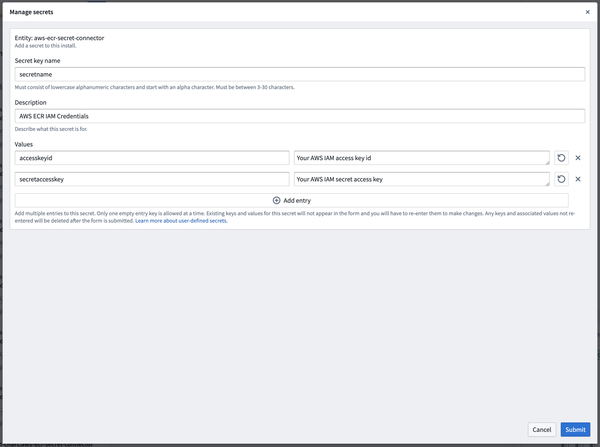
-
-
After the secret has been applied to the Entity, add the following overrides to the
aws-ecr-secret-connectorHelm chart deployed in your cluster.Copied!1 2 3 4 5 6 7 80.33.0: overrides: ecr: registries: - address: <ECR-URL> region: <REGION> credential-secret: "{{ preprocess .Values.apollo.secrets.ecrcreds.k8sSecretName }}" fips-enabled: <FIPS-ENABLED>Where:
<ECR-URL>: The URL to your ECR registry.<REGION>: The AWS region where the ECR instance is located.<FIPS-ENABLED>: Eithertrueorfalsedepending on your desired configuration.
You can reference the secret you created in Apollo using the following syntax:
{{ preprocess .Values.apollo.secrets.<secret-name>.k8sSecretName }}. Substitute<secret-name>with the name of your secret. -
Once Apollo applies the updated config, the
REGISTRY_CONNECTOR_STATUShealth check will inform you if the secret connector has successfully generated credentials for your registry.
You can repeat the above steps for any number of ECR registries you want to connect to Apollo by adding each registry config to the registries YAML array in the Entity's config overrides.